Guide for Drupal Single Sign On (SSO) using Salesforce as Identity Provider (IDP)
This document will help you in configuring SAML Single Sign-On (SSO) between Salesforce and your Drupal site. By following this guide, you can enable users to log in to your Drupal site using their Salesforce credentials, making it an Identity Provider.
The Drupal SAML SP 2.0 Single Sign On (SSO) module is compatible with Drupal 7, Drupal 8, Drupal 9, and Drupal 10.
Prerequisite:
- Install and activate the SAML SP 2.0 Single Sign On (SSO) - SAML Service Provider module on your Drupal site. Click here to check out the module installation step.
Setup Video:
Drupal SAML SP Metadata:
-
After installing the module on your Drupal site, in the Administration menu, navigate to Configuration -> People -> miniOrange SAML Login Configuration. (/admin/config/people/miniorange_saml/idp_setup)
-
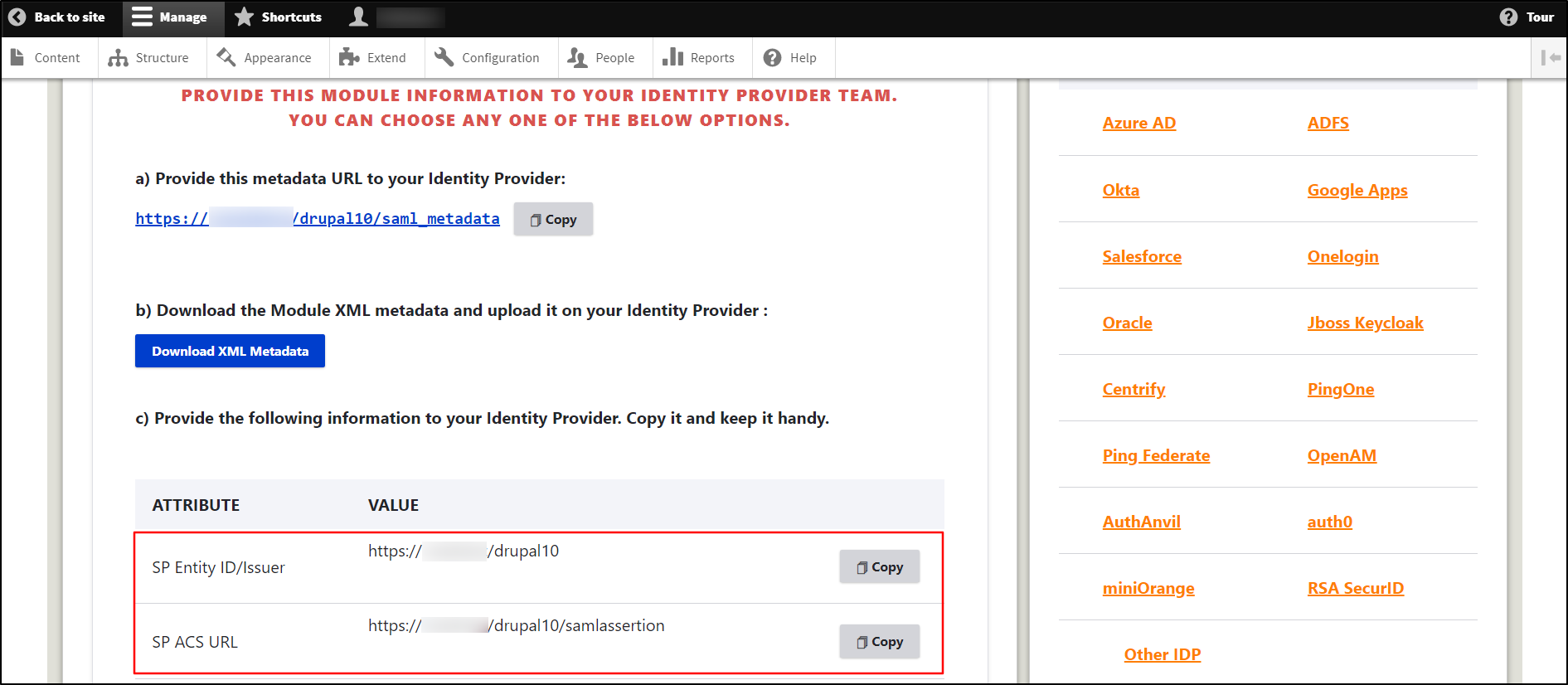
Copy the SP Entity ID/Issuer and the SP ACS URL from the Service Provider Metadata tab. Keep it handy. (This is required to configure Salesforce as IdP.)
Configure SAML Single Sign-On Application in Salesforce:
- Login into your Salesforce account.
-
In the top right corner, click on the setting Icon. Expand it and click on Setup.
- Navigate to the Quick Find box from the left side.
-
Enter Identity Provider, then select Identity Provider.
-
Click on Enable Identity Provider button.
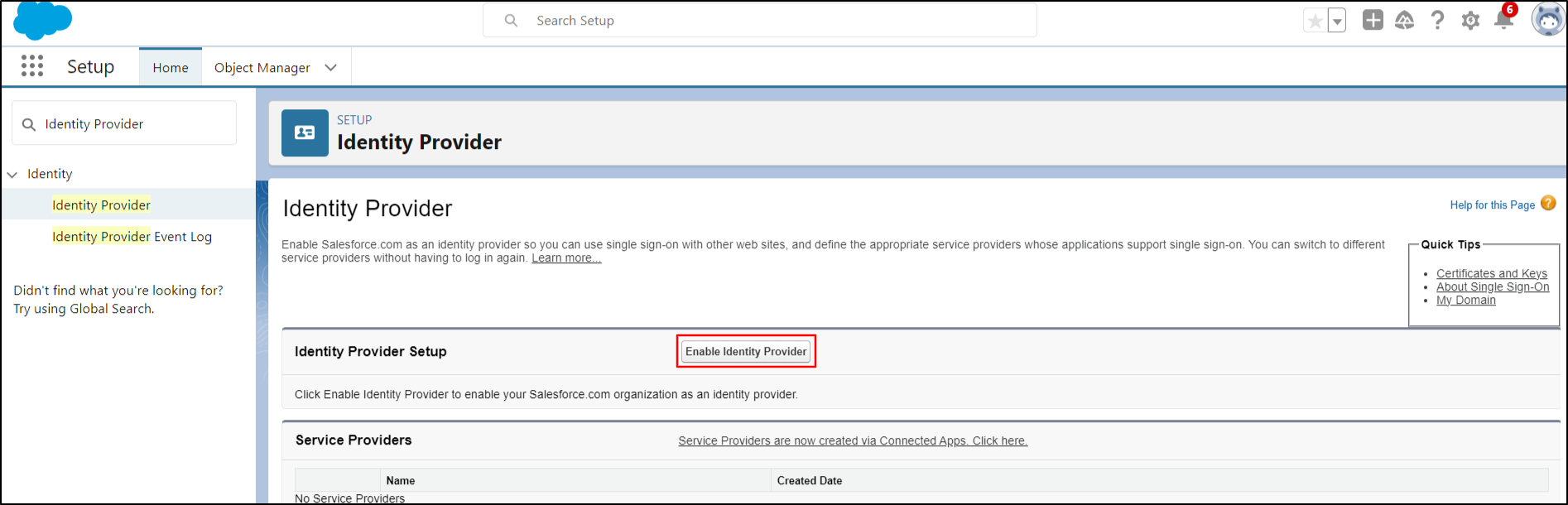
-
Then, click on Save button to proceed.
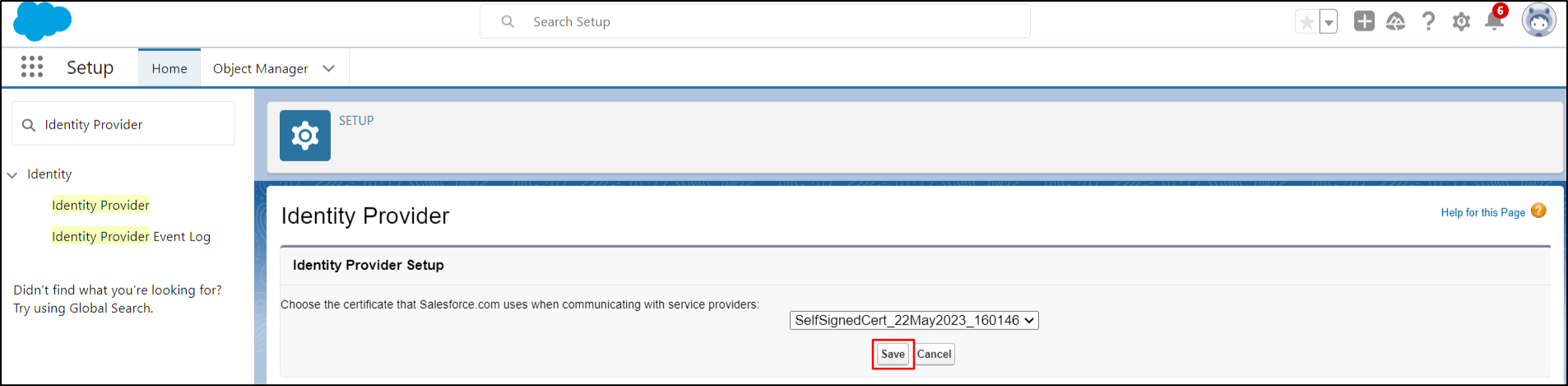
- Click on the Download Metadata button. Keep the downloaded metadata file handy. This is needed to configure Drupal as SAML Service Provider.
-
Now, click on Service Providers are now created via Connected Apps. Click here link. You will be redirected to New Connected App configurations page.
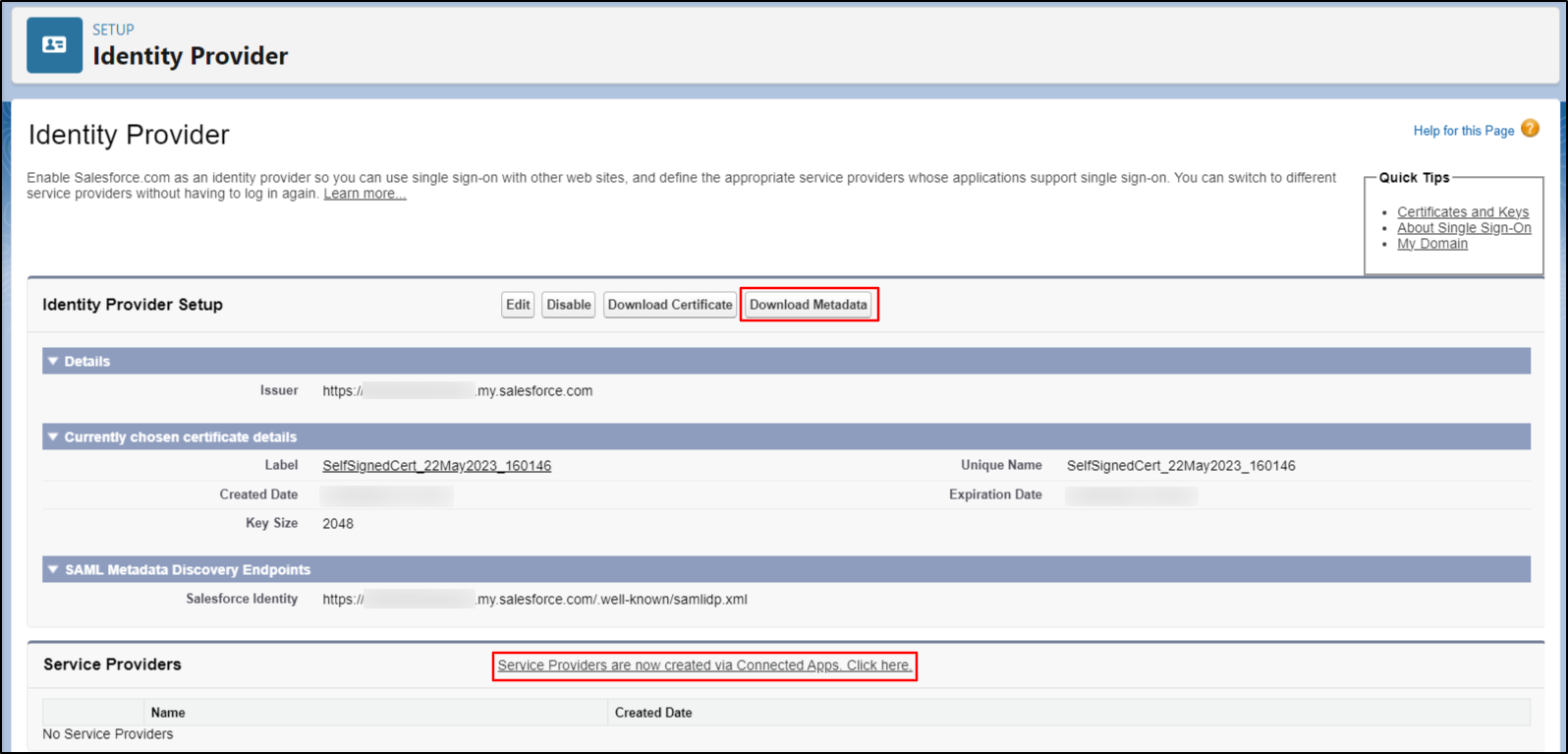
-
On the New Connected App, provide the following information.
- In Basic Information:
- Enter the name of Application in Connected App Name text field.
- After you enter the Connected App Name the API Name will be automatically generated.
-
Enter your current email address in the Contact Email text field.

-
Under Web App Settings section, check the Enable SAML checkbox and provide the required information into the corresponding text field from the Service Provider Metadata tab of the module.
Salesforce Field Service Provider Information (Drupal) Entity ID SP Entity ID / Issuer ACS URL SP ACS URL Subject Type Username Name ID Format urn:oasis:names:tc:SAML:2.0:nameid-format:persistent 
- In Basic Information:
- Scroll down and click on Save button to save your configuration.
Assign a Profiles to your Salesforce Application:
- Navigate to the Quick Find box from left navigation panel.
- Search for Manage Connected Apps, then select Manage Connected Apps.
-
Select the Application that you have created on Salesforce. For, example Drupal.
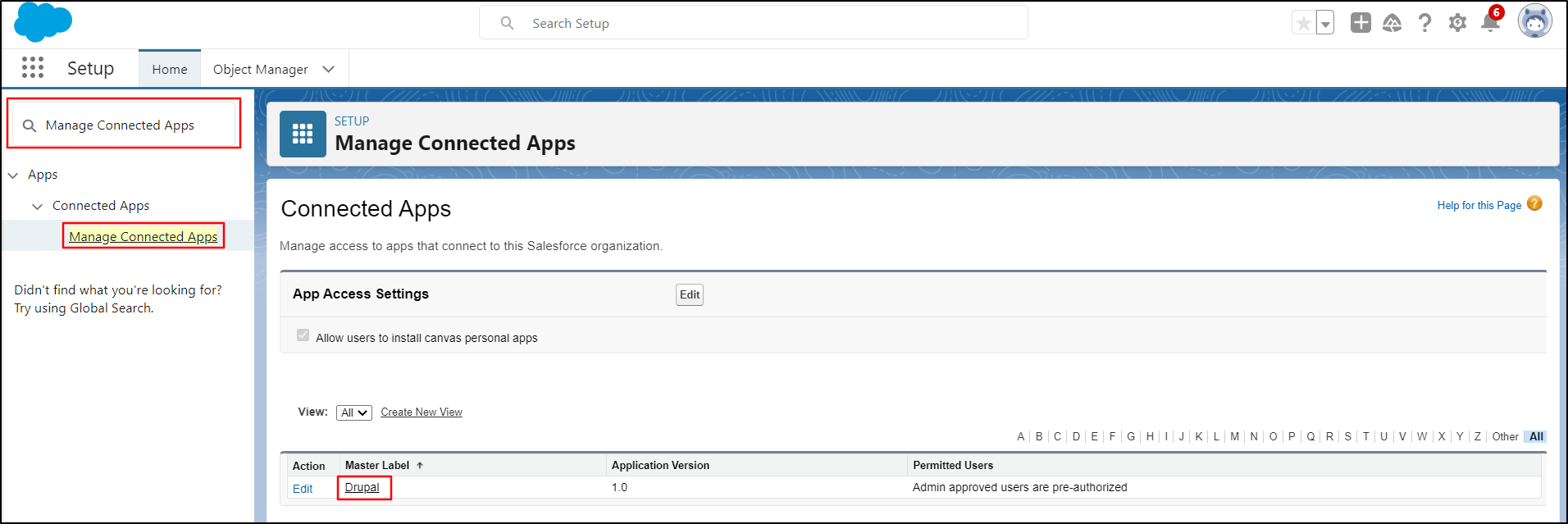
-
Scroll down to Profiles and click on Manage Profiles button.
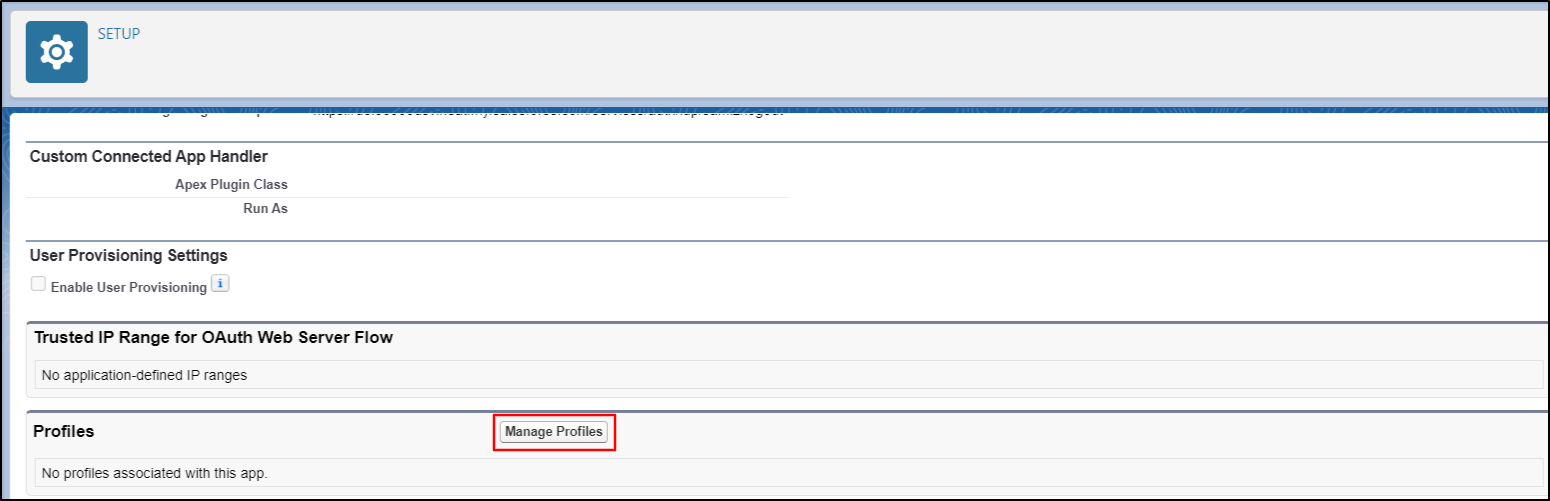
-
Select the profiles you want to give access to login through this app. Click on the Save button.
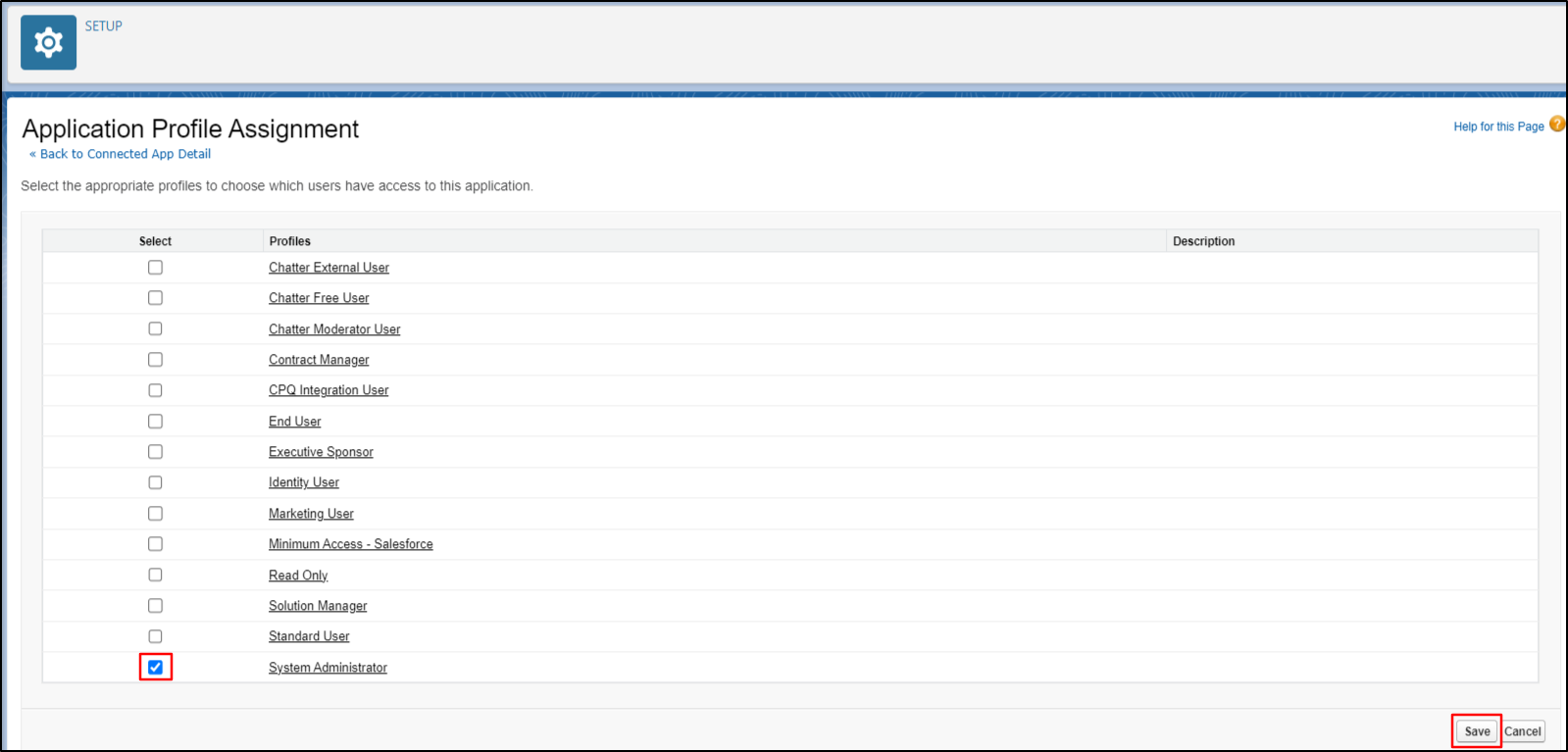
The profile has been successfully assigned to your application.
Configure Drupal as SAML Service Provider:
- Go to your Drupal site. Navigate to the Service Provider Setup tab of the module and click on the Upload IDP Metadata.
-
In the Upload Metadata File field, select the XML metadata file that you downloaded from Salesforce. Then, click on the Upload File button.
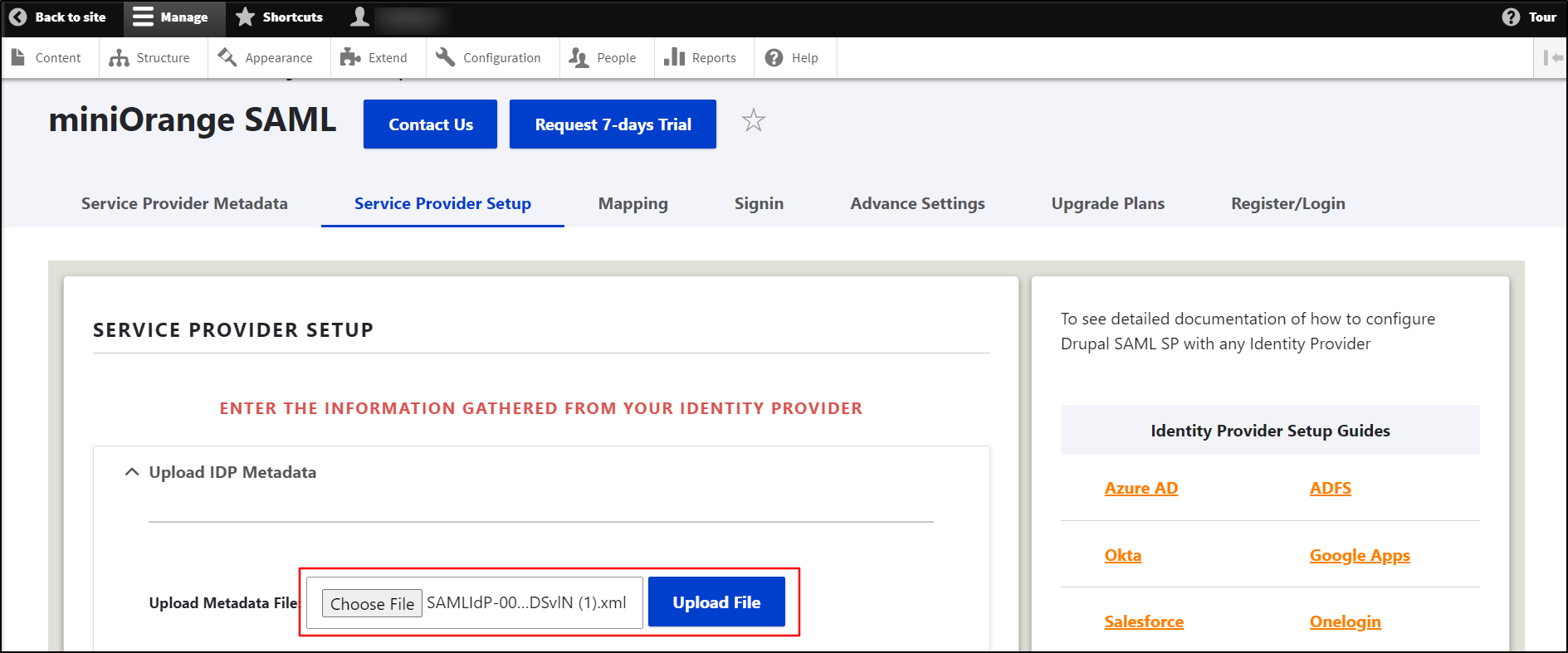
If you need to update your Identity Provider Name, follow these steps:
- Under Action, select the Edit link.
- Enter Salesforce as the name of Application in the Identity Provider Name text field.
- After you have updated your Identity Provider Name, scroll to the bottom and click on the Save Configuration button.
-
After successfully saving the configurations, click on the Test link to test the connection between Drupal and Salesforce.
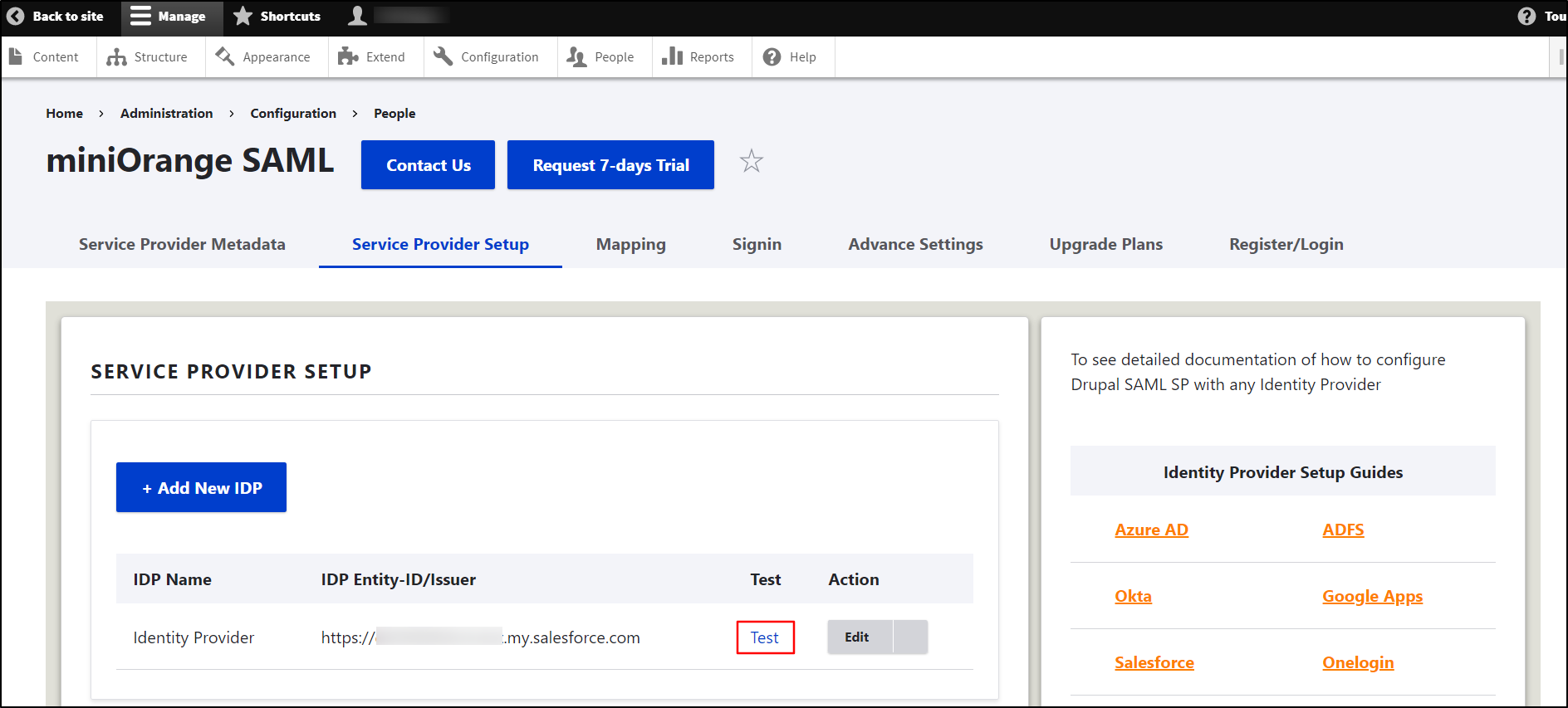
- On a Test Configuration popup, if you don't have an active session in the same browser, you will be asked to sign in to Salesforce. After successfully logging into Salesforce, you will be provided with a list of attributes that are received from the Salesforce.
-
Scroll down and click on Done button.
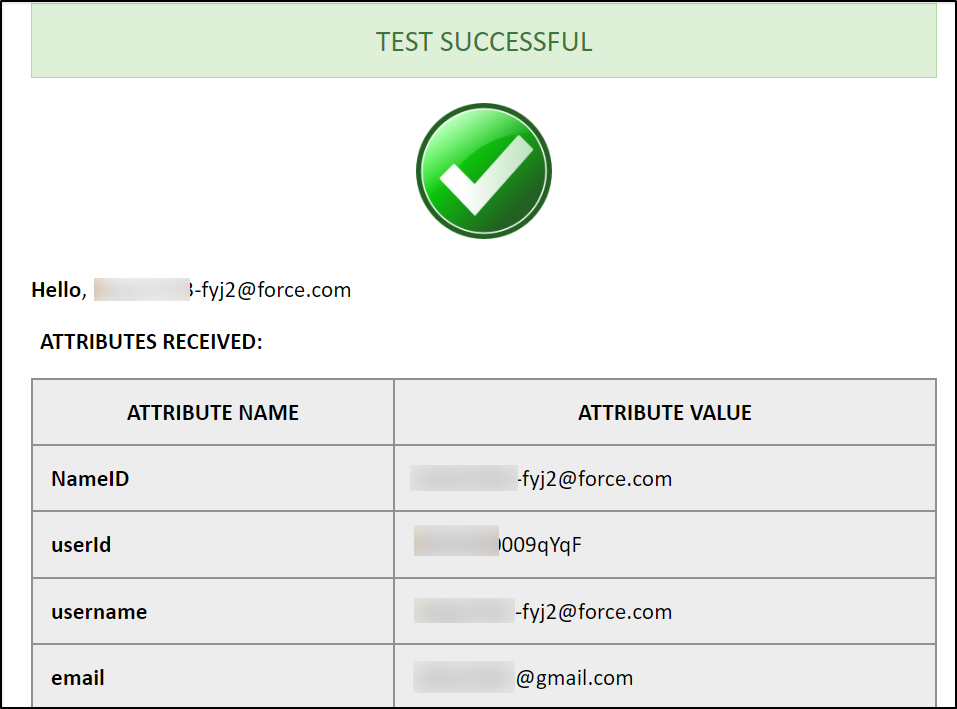
Congratulations! You have successfully configured Salesforce as Identity Provider and Drupal as Service Provider.
If you face any issues in test configuration you can reach out to us at drupalsupport@xecurify.com with a screenshot of the test configuration window.
How does SAML SSO login work?
- Open a new browser/private window and navigate to the Drupal site login page.
- For SP initiated SSO on your Drupal, click on the Login using Identity Provider (Salesforce) link.
-
You will be redirected to the Salesforce login page, wherein the user will enter their Salesforce credentials. Once you have successfully logged in, Salesforce users will be able to access your Drupal site within a seconds.
Help improve this page
You can:
- Log in, click Edit, and edit this page
- Log in, click Discuss, update the Page status value, and suggest an improvement
- Log in and create a Documentation issue with your suggestion
 Support for Drupal 7 is ending on 5 January 2025—it’s time to migrate to Drupal 10! Learn about the many benefits of Drupal 10 and find migration tools in our resource center.
Support for Drupal 7 is ending on 5 January 2025—it’s time to migrate to Drupal 10! Learn about the many benefits of Drupal 10 and find migration tools in our resource center.










