DDEV is the official local development tool of Drupal. And like Drupal, DDEV depends on the support of the open source community.
DDEV is the official local development tool of Drupal. And like Drupal, DDEV depends on the support of the open source community.This project is not covered by Drupal’s security advisory policy.
This module provides a Drush command to identify and remove any malware and phishing code injected into the site after a cyber attack. The module looks for any unsafe code injected into text area fields in entities and helps to remove them.
Malware
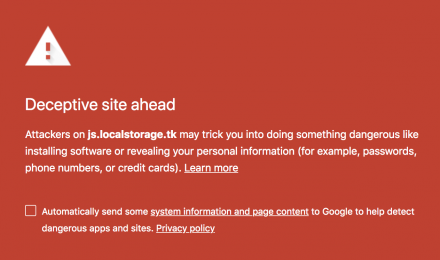
These websites contain code that installs malicious software onto visitors’ computers, either when a user thinks they are downloading legitimate software or without a user’s knowledge. Hackers can then use this software to capture and transmit users' private or sensitive information. Our Safe Browsing technology also scans and analyzes the web to identify potentially compromised websites.
Phishing
These websites pretend to be legitimate so that they can trick users into typing in their usernames and passwords or sharing other private information. Web pages that impersonate legitimate bank websites or online stores are common examples of phishing sites.
How does the module identify unsafe code?.
Module loops through the nodes and other entities of the website and keep records of scripts injected into content, those could be safe and unsafe, the Drusha command will output them so you can choose which ones are safe and which ones are not. Then the module will remove all unsafe code.
How to use?
- Install the Deceptive Site Remover module as you would normally install a contributed Drupal module. Visit https://www.drupal.org/docs/7/extend/installing-modules for further information.
- Run
drush rucordrush remove-unsafe-codeand follow the command line instructions.
Need help?
Contact me here https://www.heididev.com/hire
Project information
- Project categories: Security
42 sites report using this module
- Created by hypertext200 on , updated
This project is not covered by the security advisory policy.
Use at your own risk! It may have publicly disclosed vulnerabilities.