Configure Microsoft Entra ID as OAuth Provider with Drupal as OAuth Client for SSO
This document will help you configure Microsoft Entra ID or Azure AD as an OAuth provider making Drupal as an OAuth client. Following these steps will allow you to configure OAuth SSO between Microsoft Entra ID and your Drupal site such that your users will be able to log in to your Drupal site using their Microsoft Entra ID credentials.
We provide Drupal OAuth & OpenID Connect Login - OAuth2 Client SSO Login module which is compatible with Drupal 7, Drupal 8, Drupal 9, and Drupal 10.
You can check our module reviews and ratings here.
Prerequisite:
- Install and activate the OAuth & OpenID Connect Login - OAuth2 Client SSO Login module on your Drupal site. Click here to check out the module installation step.
Setup Video:
Steps to configure Drupal as OAuth Client:
-
Once you have installed the module, go to the Configuration tab, and click on the miniOrange OAuth Client Configuration.
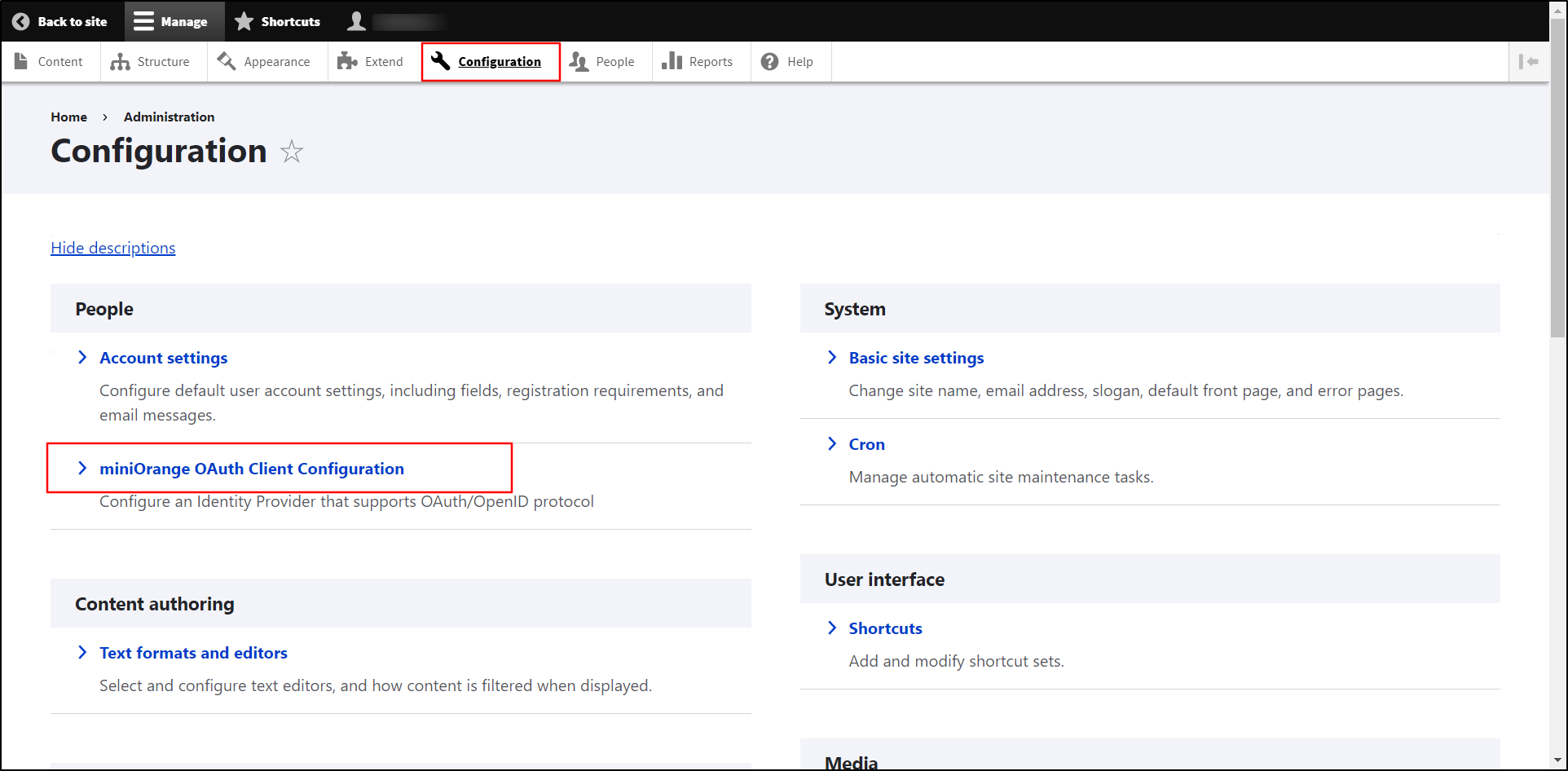
- Provide the following information within the Configure OAuth tab:
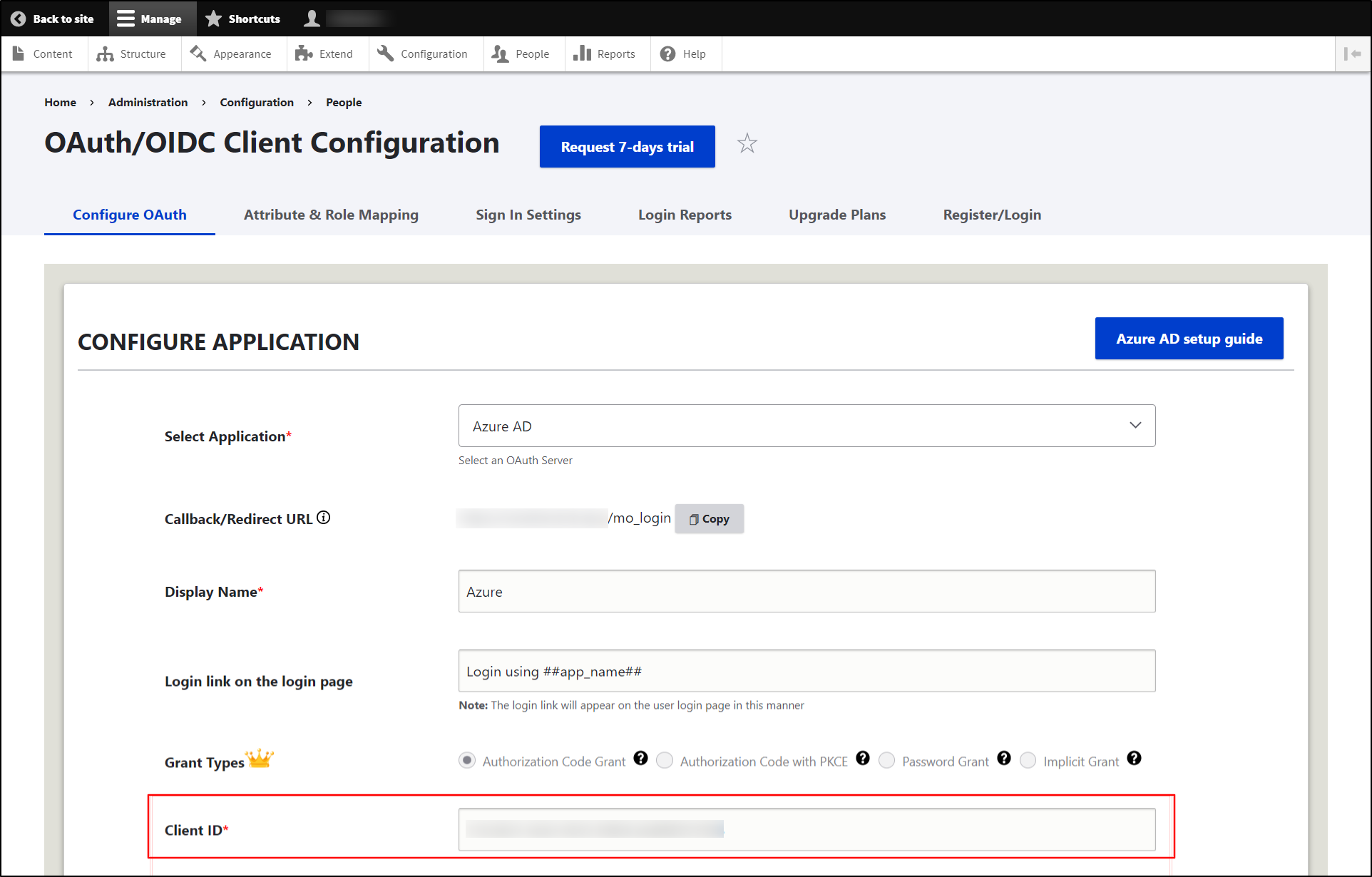
- Select Microsoft Entra ID (Azure AD) from the Select Application dropdown.
- Copy the Callback/Redirect URL and keep it handy.
If your provider only supports HTTPS Callback/Redirect URLs and you have an HTTP site, please make sure to enable the 'Enforce HTTPS Callback URL' checkbox at the bottom of the tab.
-
Enter the Application name in Display Name text field. For example, Azure.
-
Configure OAuth SSO Application in Microsoft Entra ID:
- Login into your Microsoft Entra ID portal.
-
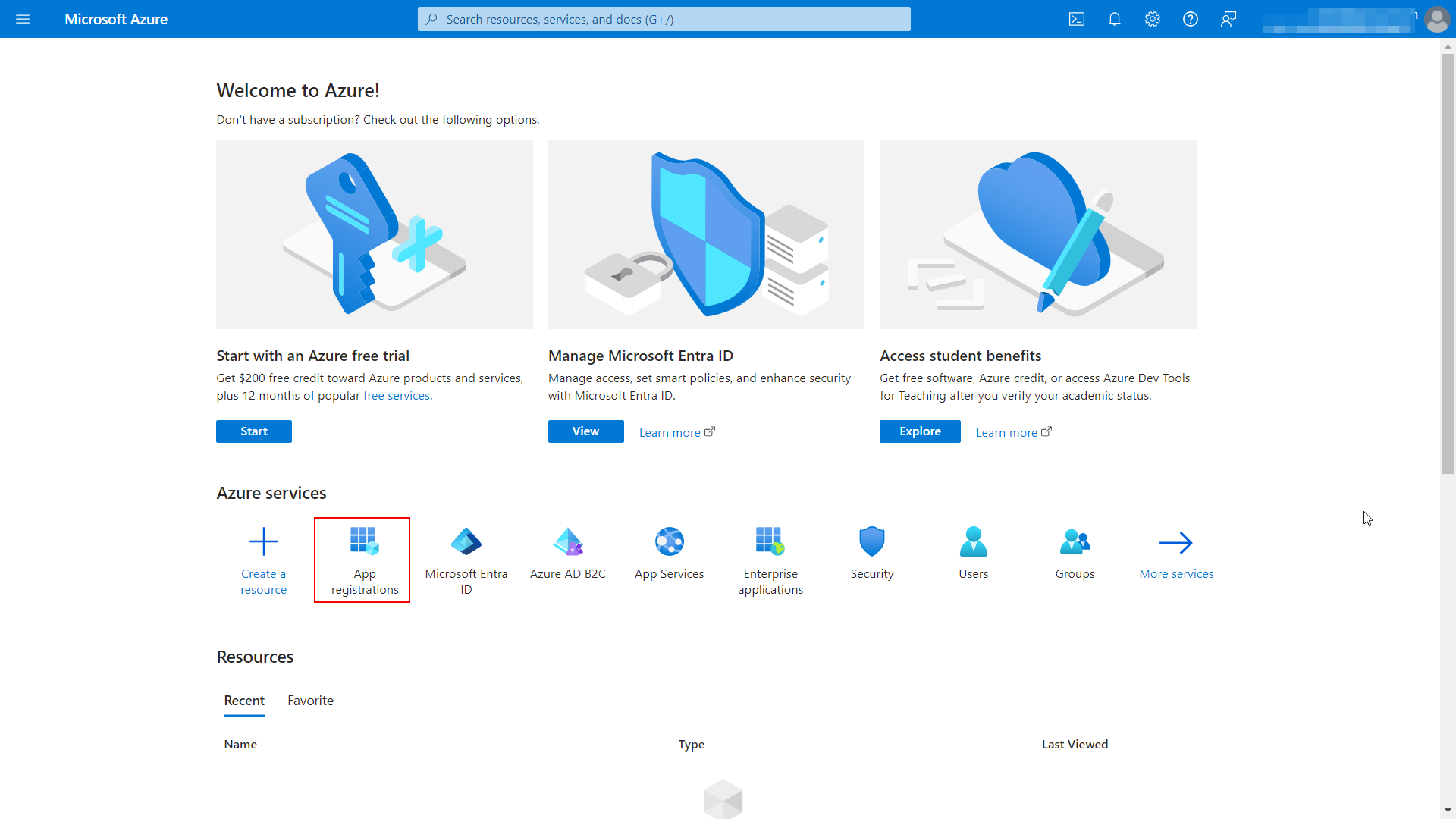
In the Azure services section, click on App registrations.
-
Then, click on New registration.
- On the Register an Application page, enter the required information:
- Name: Enter the Application Name, for example Drupal.
- Supported account types: Select the 1st option - Accounts in this organizational directory only (Test only - Single tenant). If you are not sure what to choose, you can click on the Help me choose link.
-
Under the Redirect URI (optional) from the Select a platform dropdown select Web and paste the previously copied Callback URL under the text field next to the dropdown.
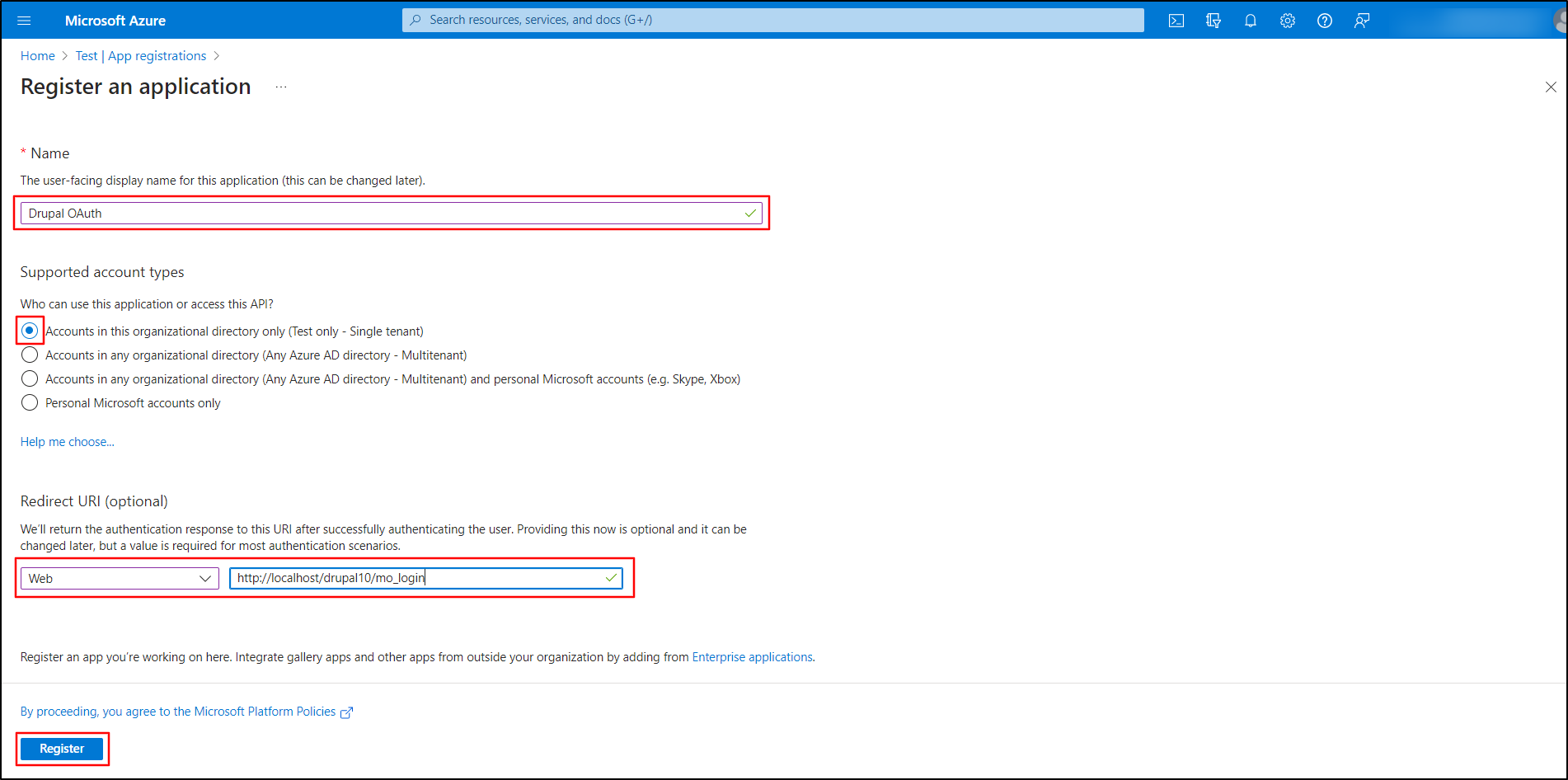
- Once done, click on the Register button.
Integrating Drupal with Microsoft Entra ID:
-
From the Microsoft Entra ID portal, copy the Application (client) ID.
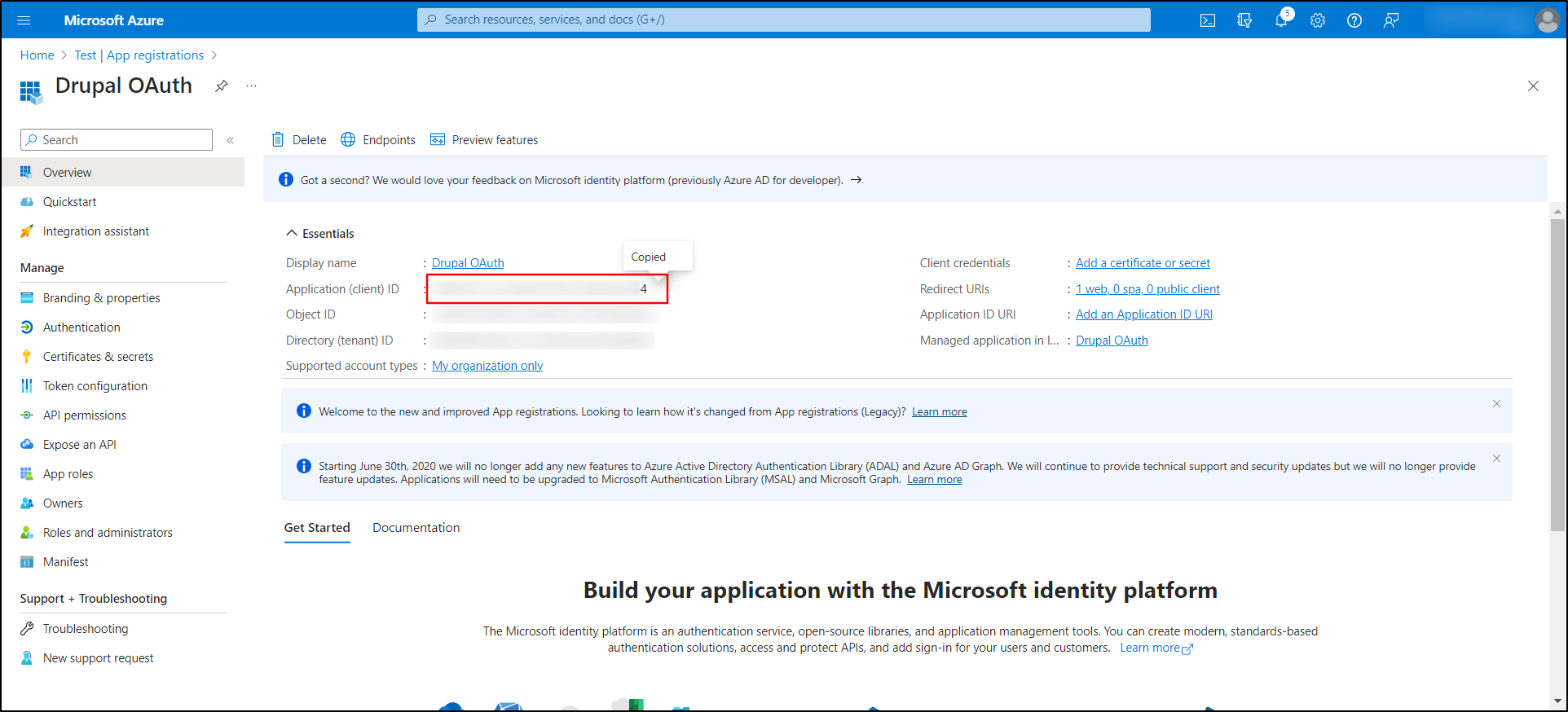
-
Navigate to the Drupal site and paste the copied Application(client) ID into the Client ID text field.
- Again, go back to the Microsoft Entra ID portal.
-
Click on Add a certificate or secret link.
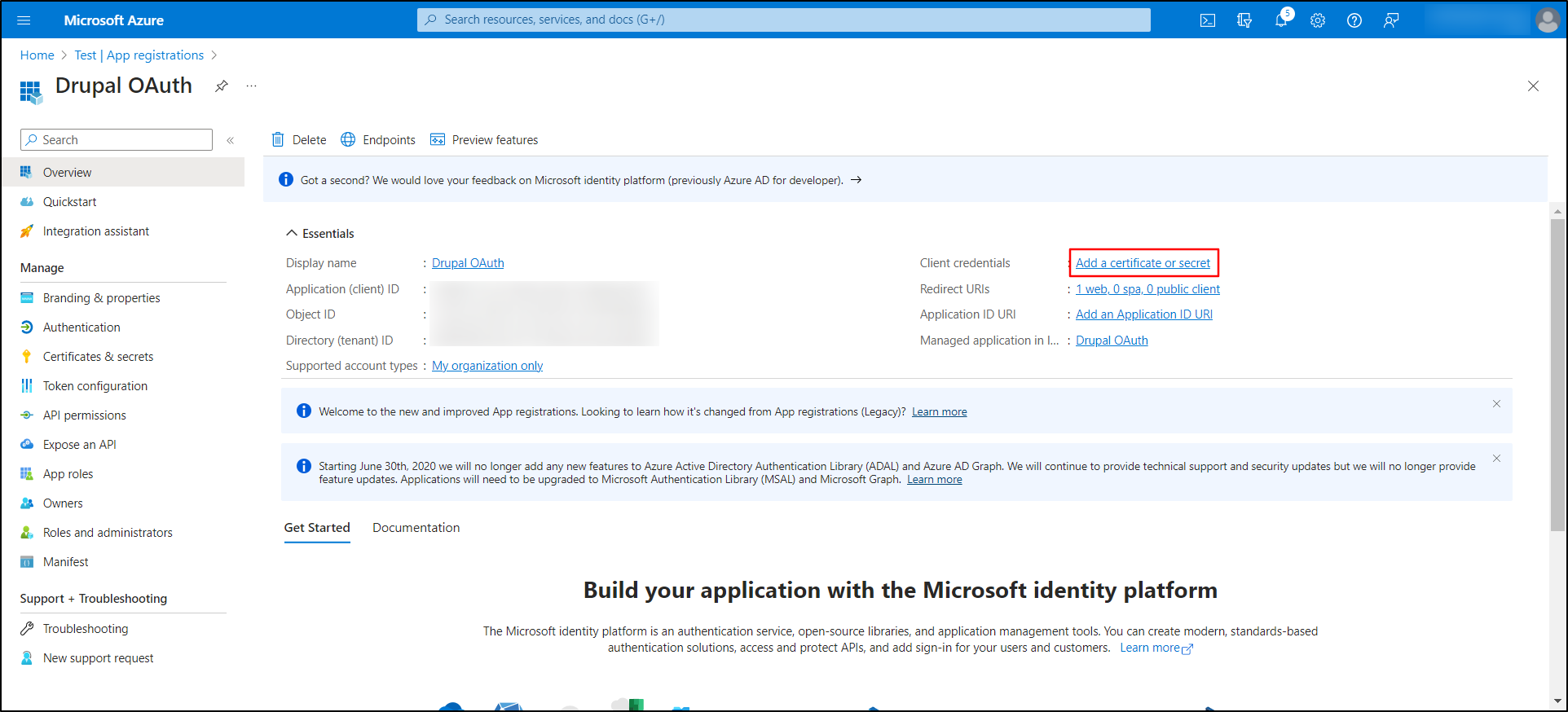
- Then, click on the New client secret button.
-
In the Add a client secret, enter the Description, and select duration of the certificate from the Expires dropdown. Click on the Add button.
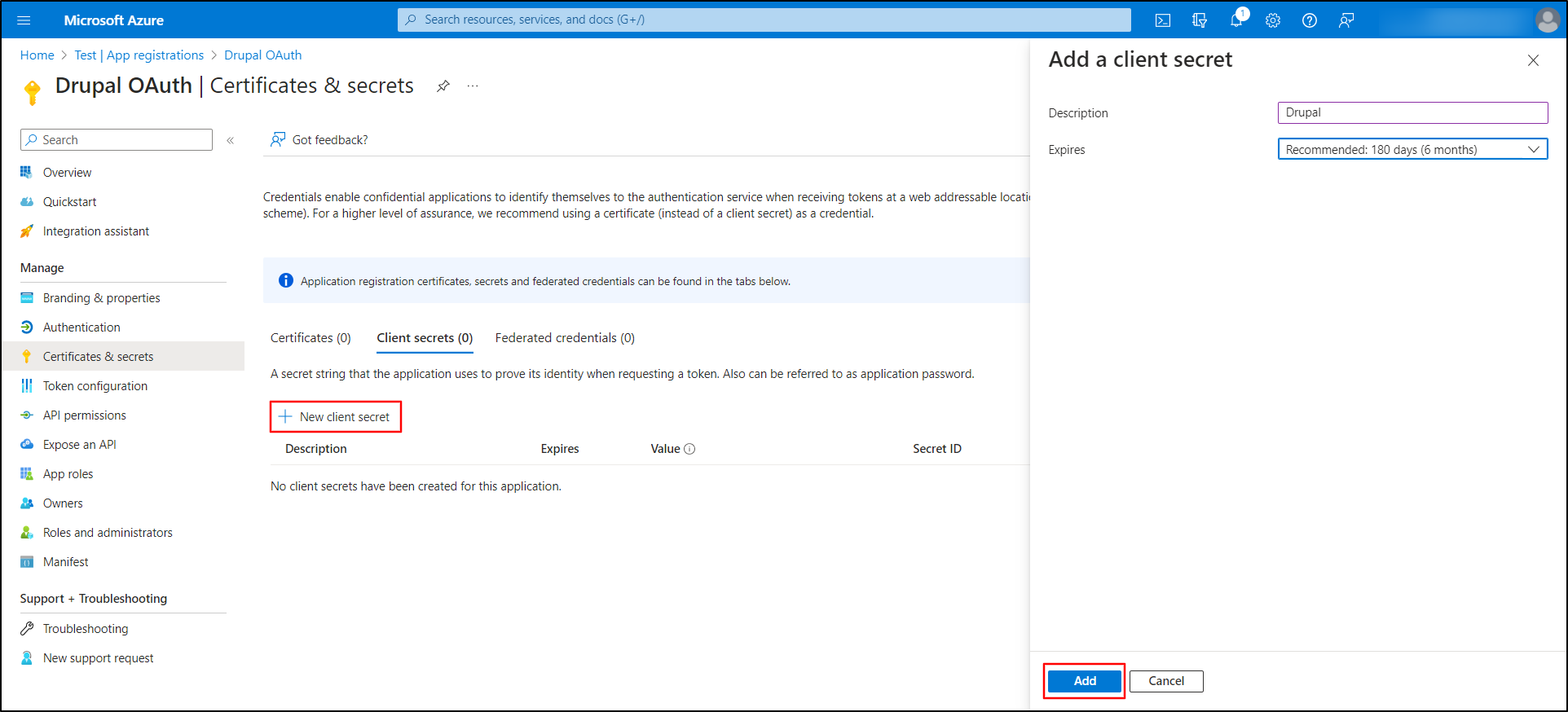
-
Copy the Value from the Client secrets tab, this is your Client Secret key.
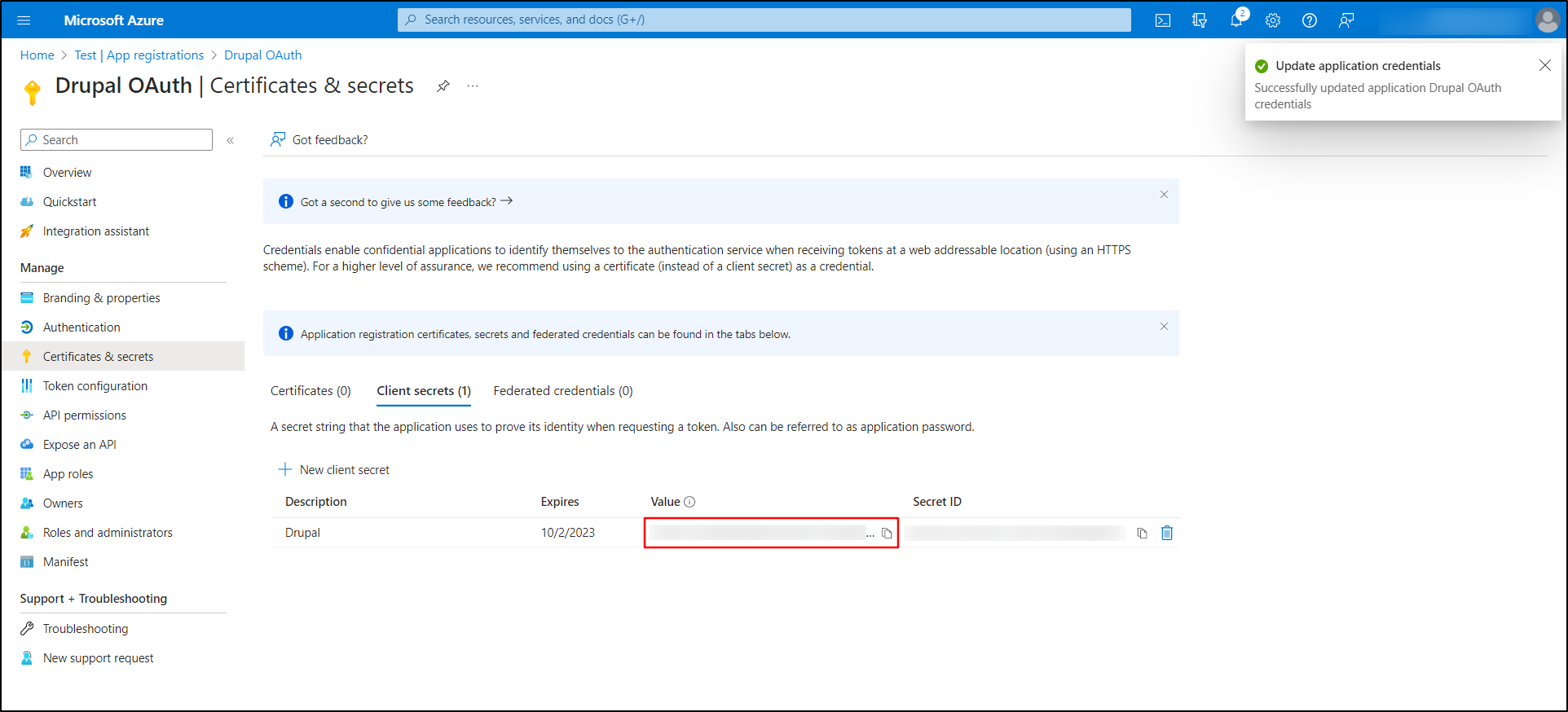
-
Then, navigate to the Drupal site and paste the copied Client secret value into the Client Secret text field.
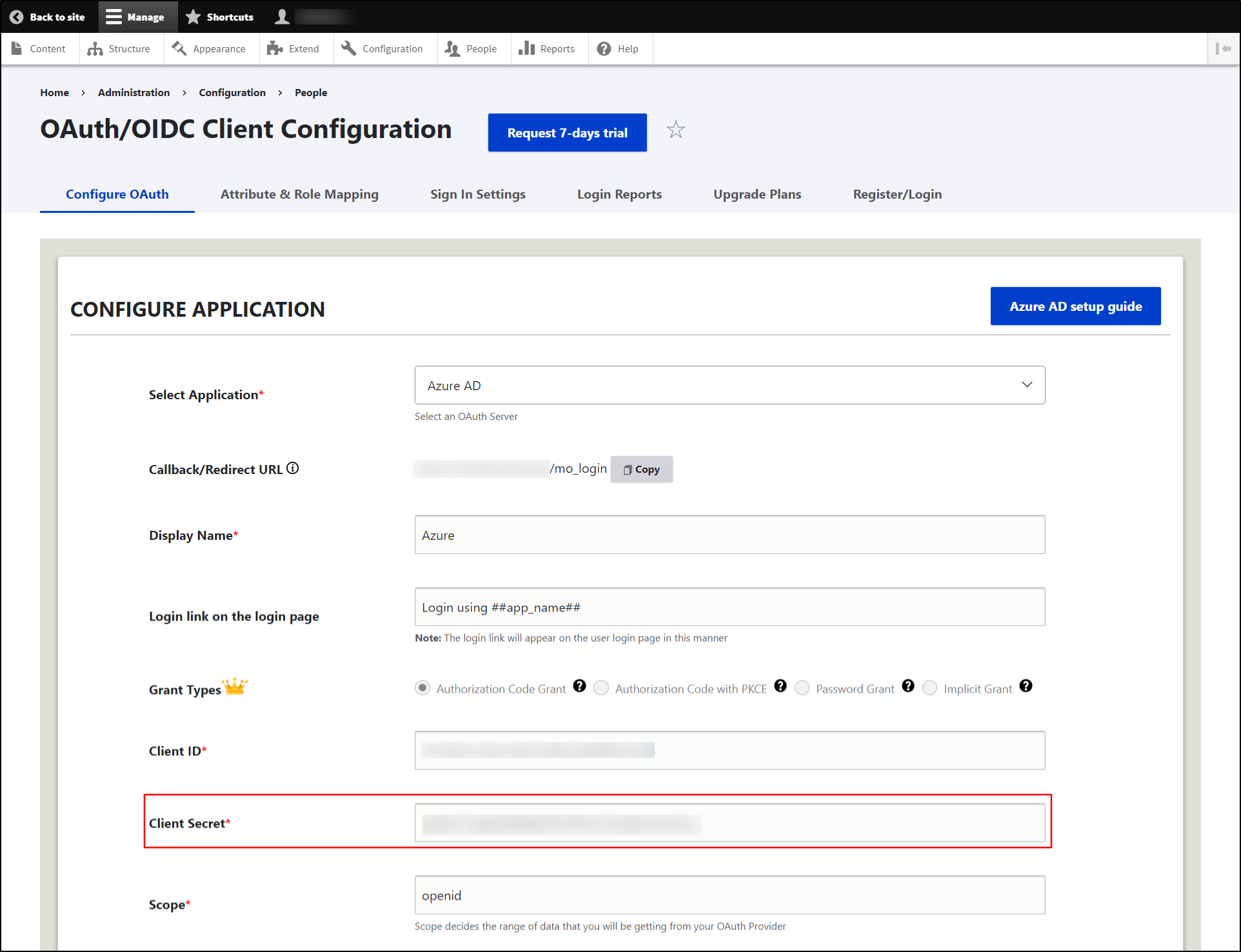
-
Go back to the Microsoft Entra ID portal and navigate to the Overview tab.
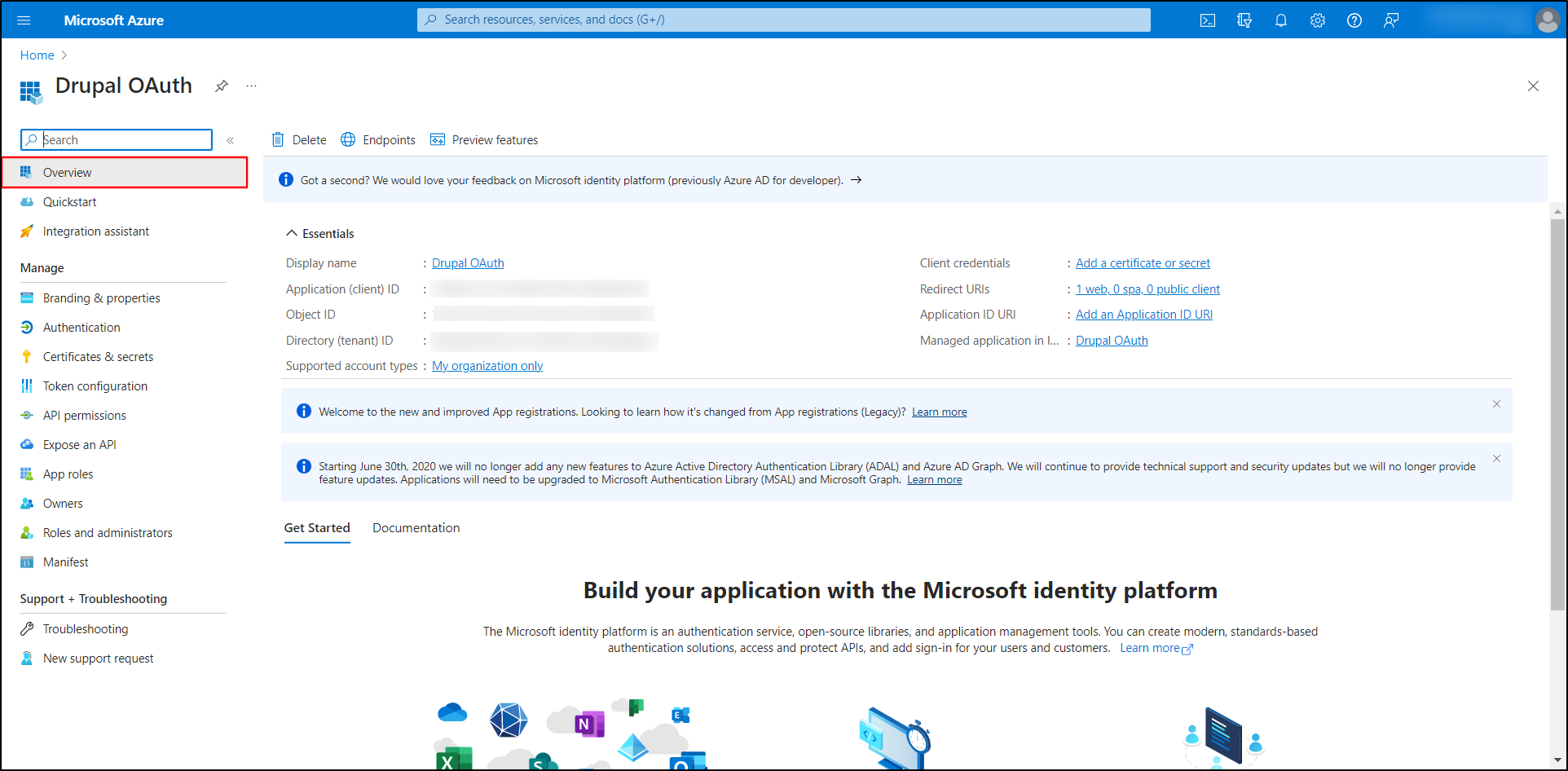
-
Under the Essentials section, copy the Directory (tenant) ID.
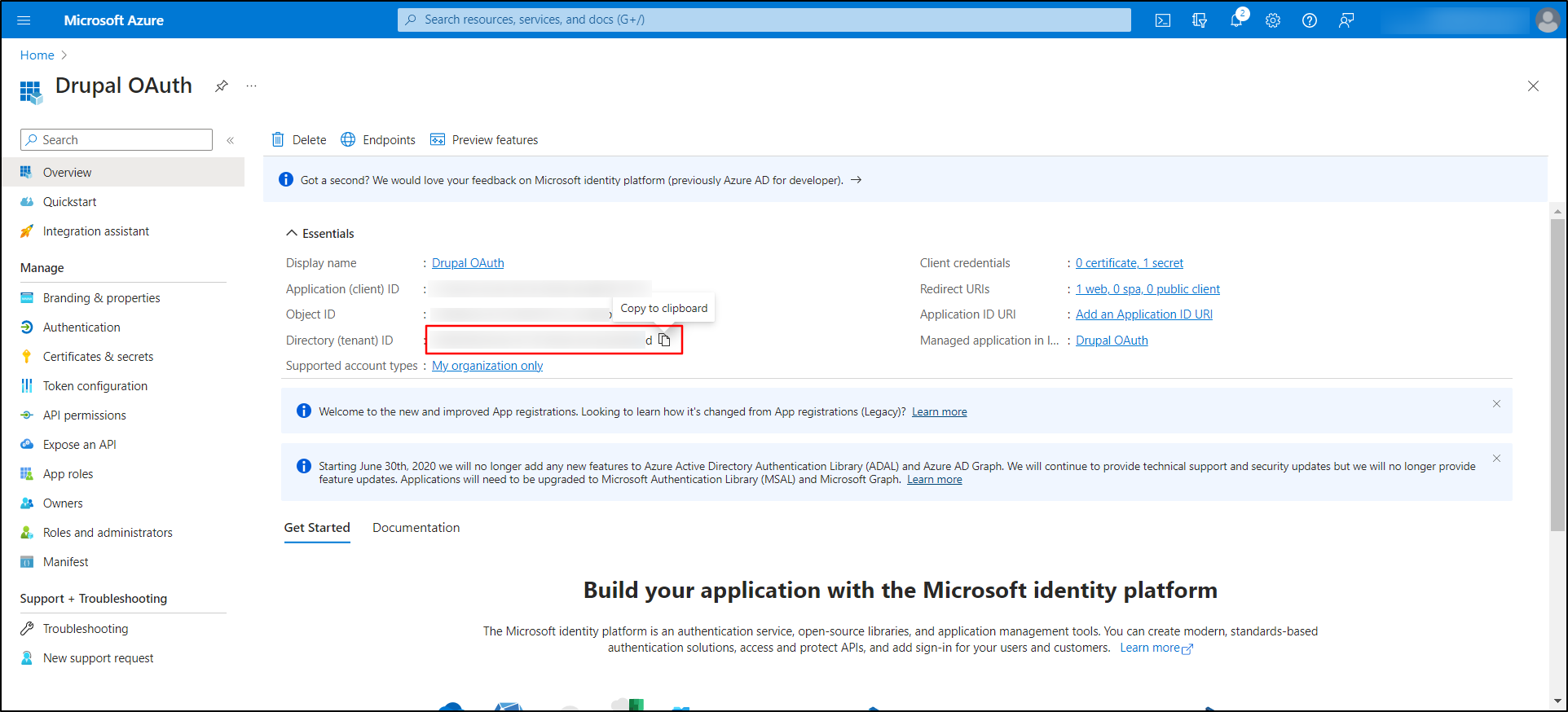
-
Navigate to the Drupal site and replace the copied Directory (tenant) ID with the {tenant-id} in the Authorization Endpoint and Access Token Endpoint text field. Once done, click on the Save Configuration button.
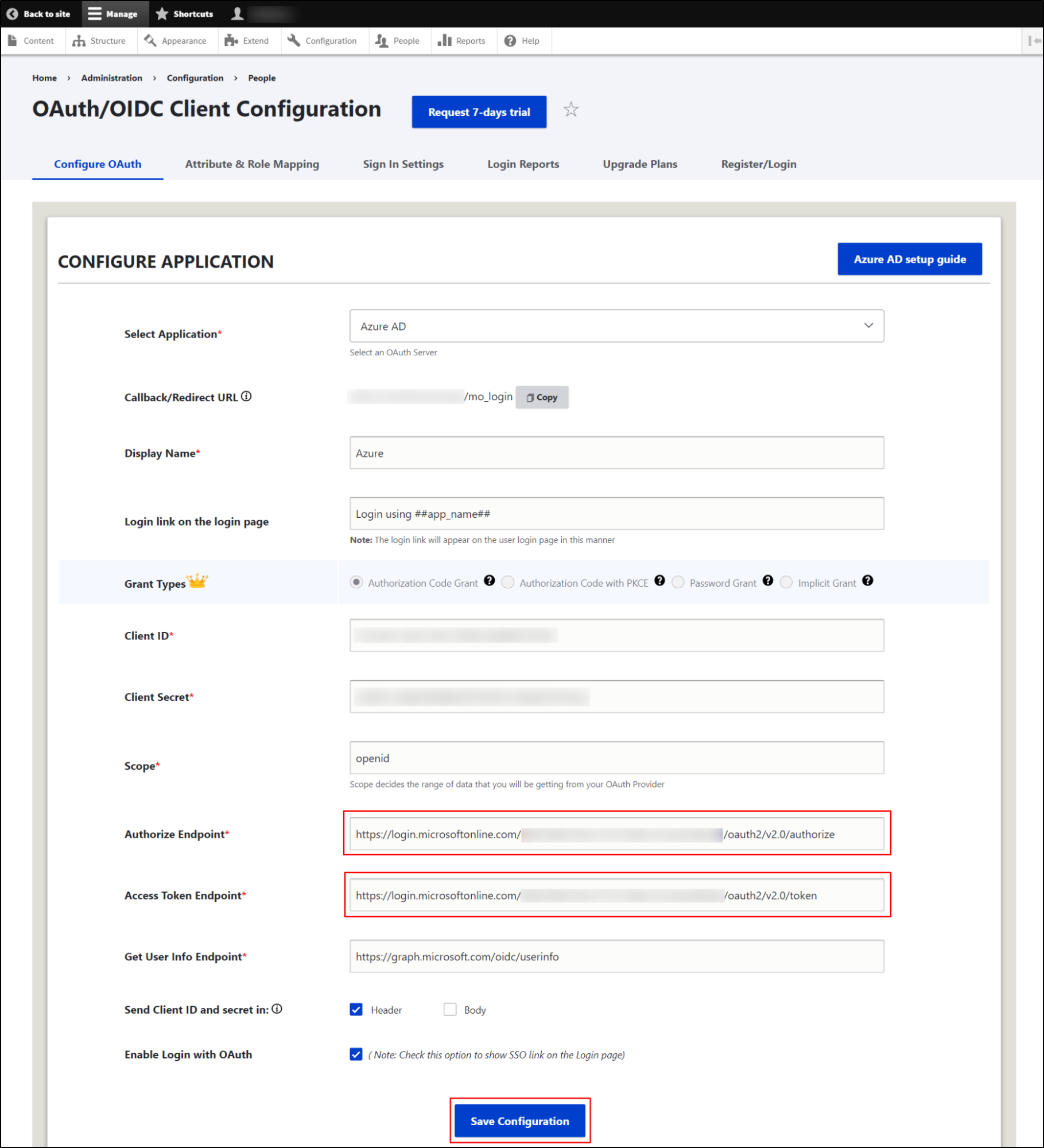
You can also refer to the Azure AD Endpoints and Scope from the table given below:
| Scope | OpenID |
| Authorize Endpoint: | https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/authorize |
| Access Token Endpoint: | https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/token |
| Get User Info Endpoint: | https://graph.microsoft.com/oidc/userinfo |
-
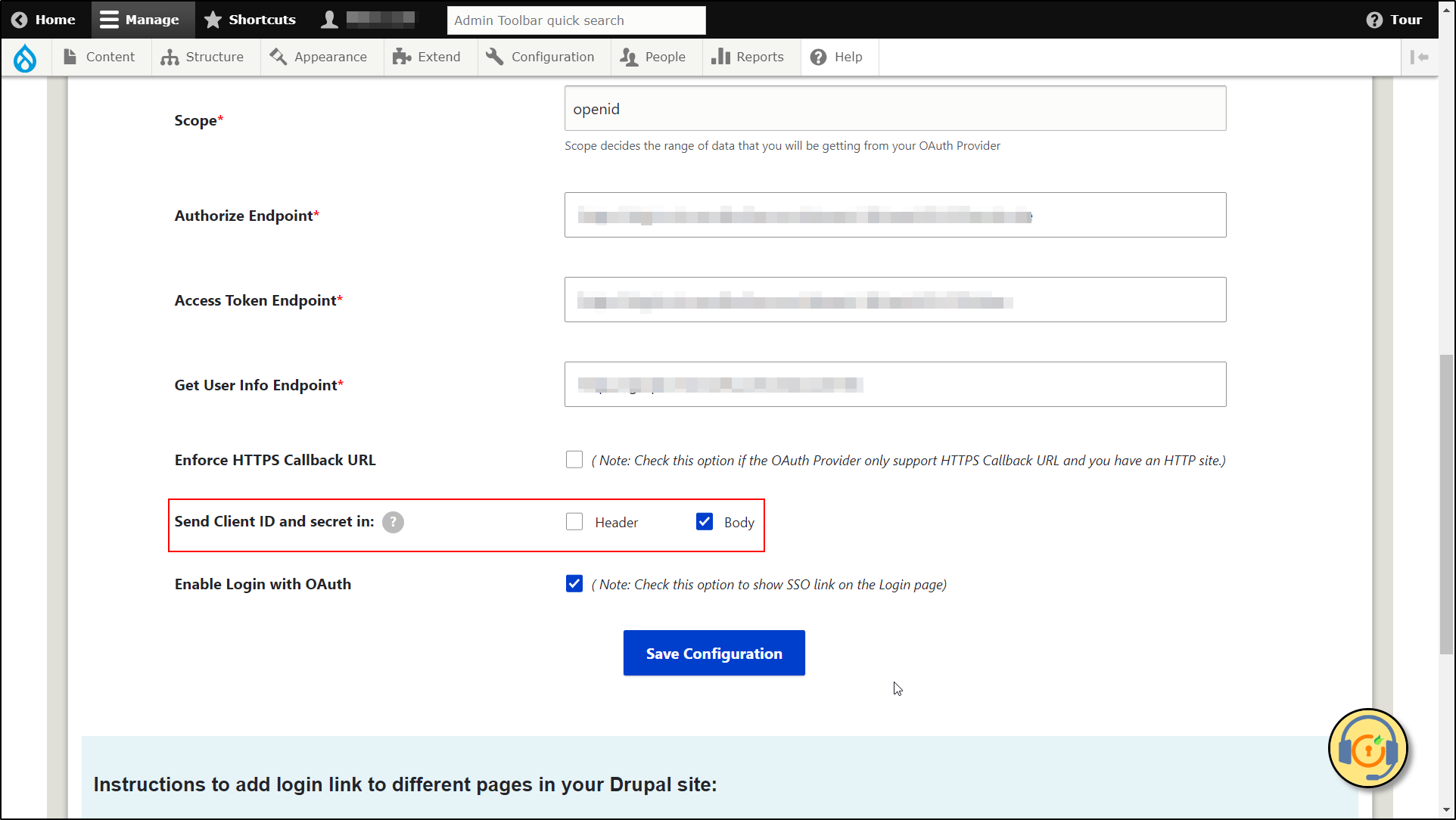
The Send Client ID and Secret in checkbox allow you to specify whether the Client ID and Secret should be included in the header or the body of the Token Endpoint Request. If you're unsure which option to select, you can stick with the default settings.
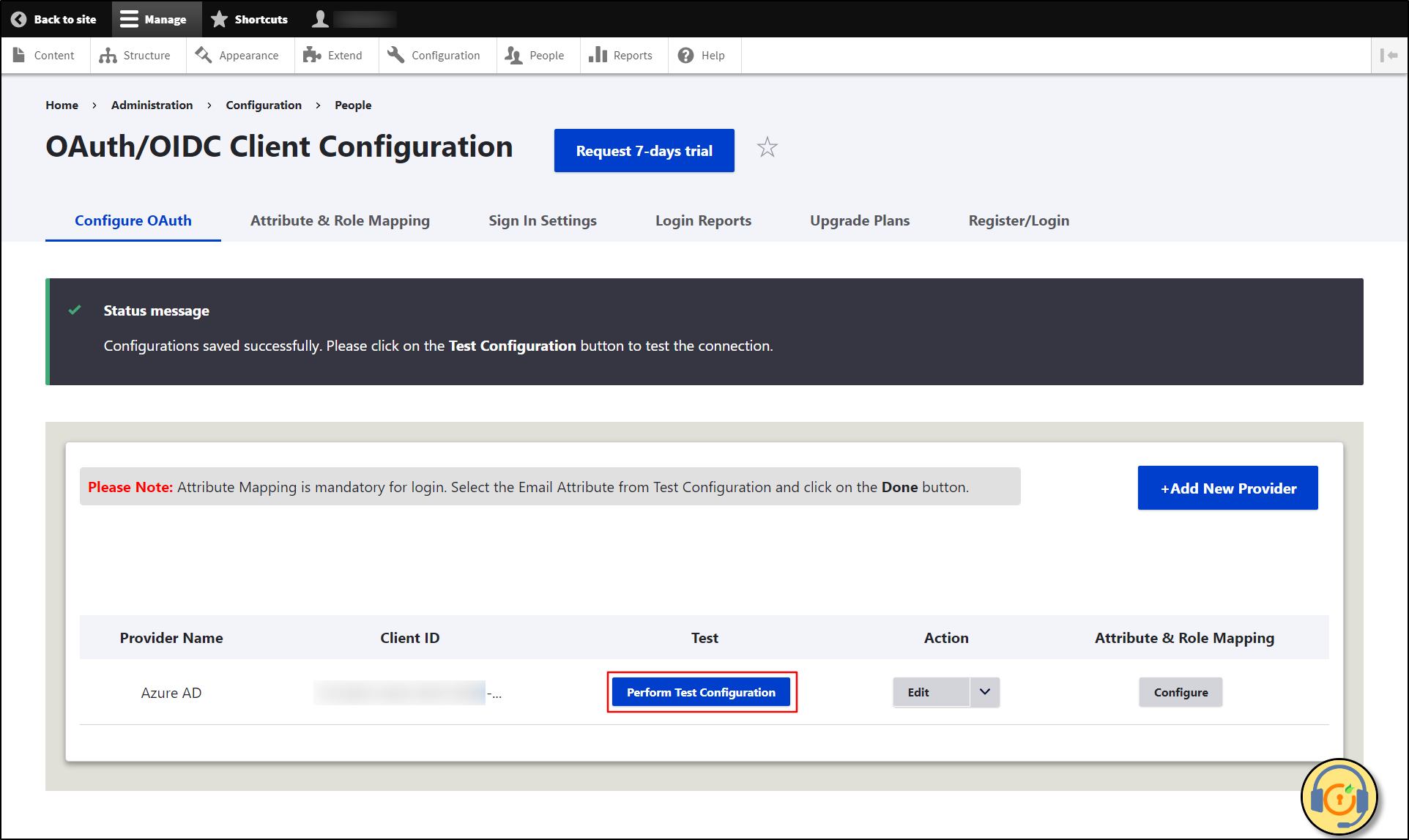
Test Configuration of Drupal with Microsoft Entra ID :
-
After successfully saving the configurations, click on the Perform Test Configuration button to check the connection between Drupal and Azure AD.
- On a Test Configuration popup, if you don't have an active session in Microsoft Entra ID on the same browser, you will be asked to sign in to your Azure AD. After successfully logging into Microsoft Entra ID, you will be provided with a list of attributes that are received from the Azure AD.
-
Select the Email Attribute (The Attribute which contains the user's email. In our case it is ‘email’) from the dropdown menu and click on the Done button.
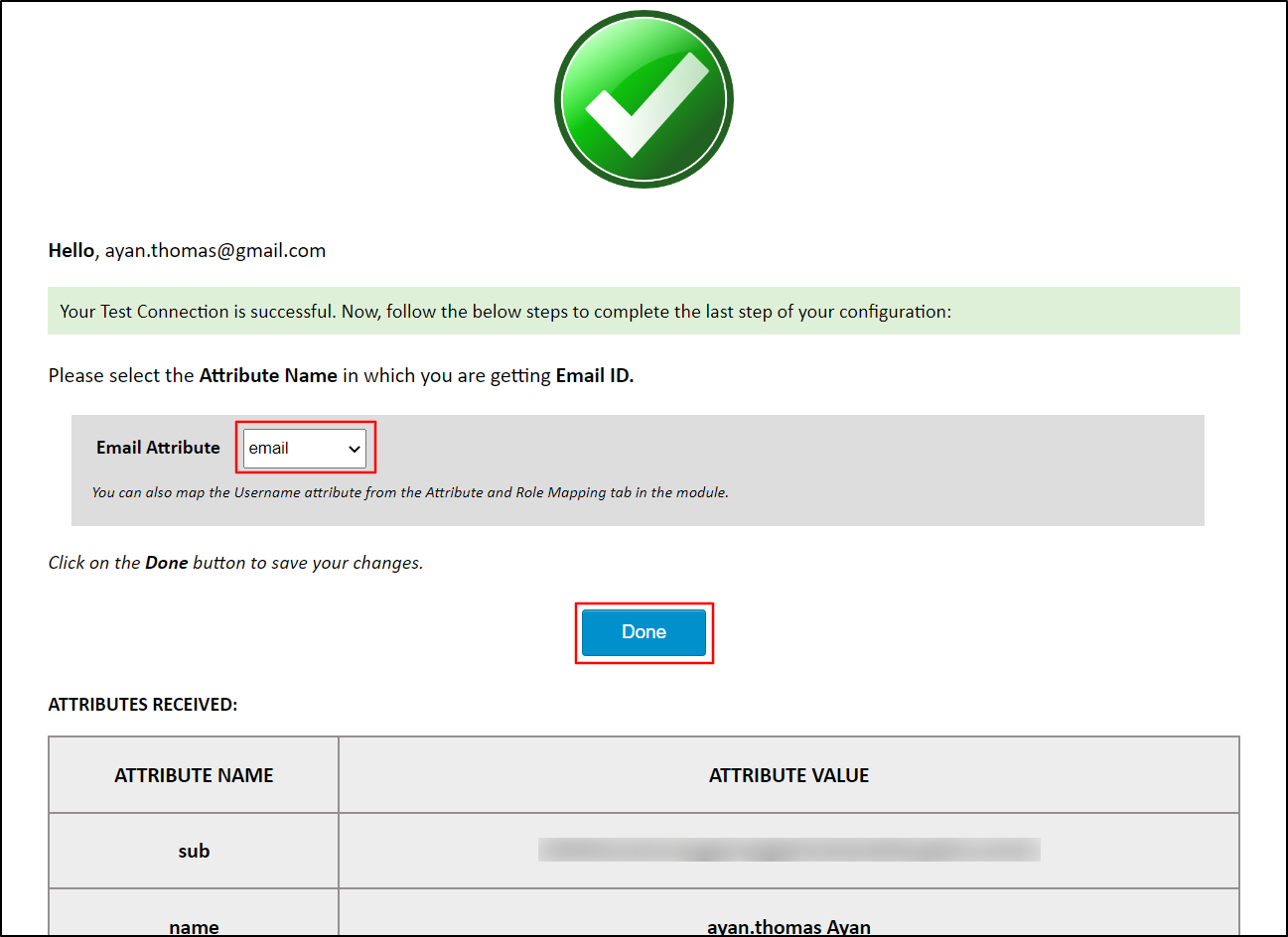
-
Once clicked on the Done button, you will be redirected to the Attribute & Role Mapping tab. Now, you can also choose the Username Attribute from the dropdown and click on the Save Configuration button.
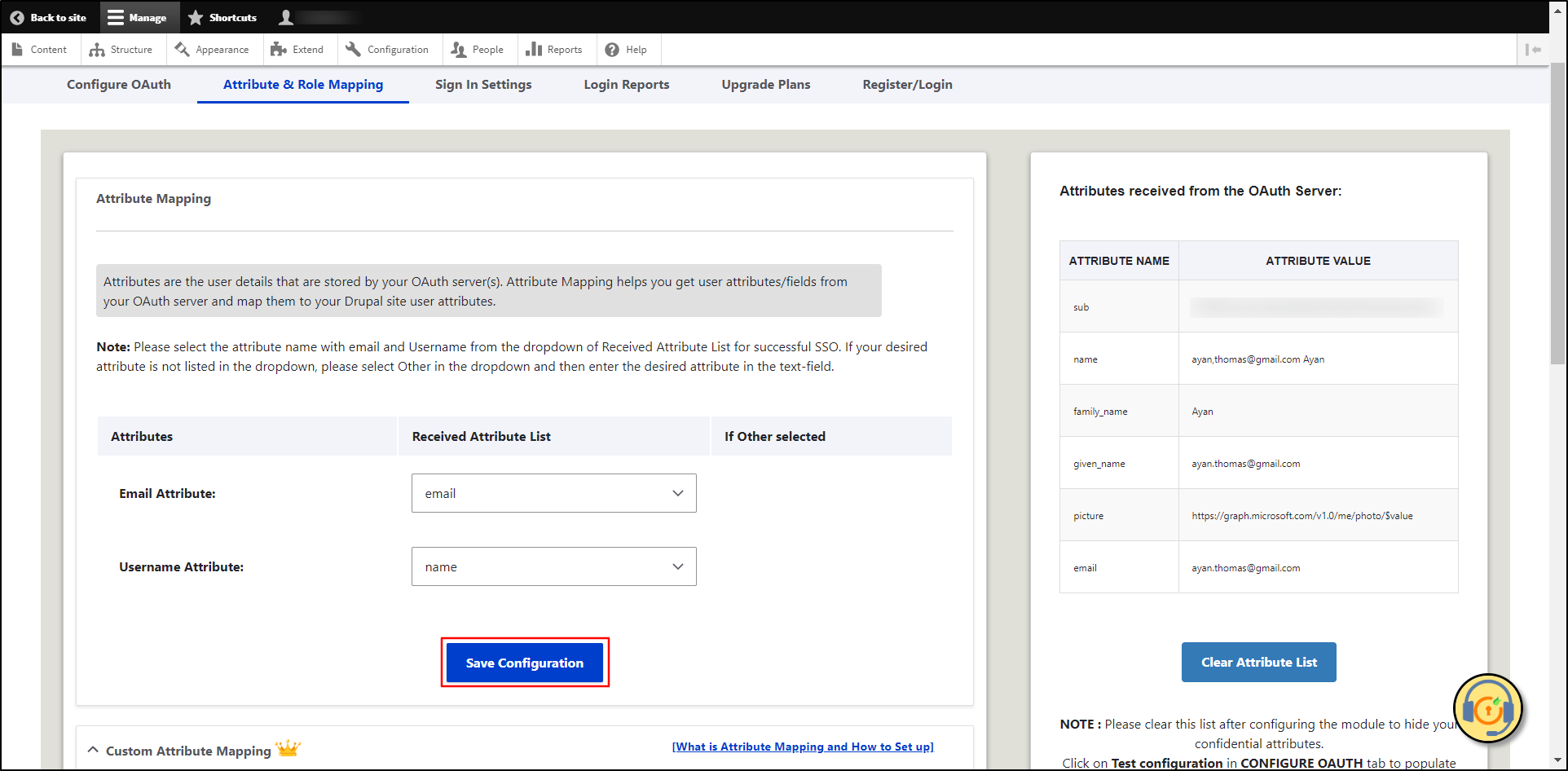
Please note: Mapping the Email Attribute is mandatory for your login to work.
Congratulations! You have successfully configured Azure AD as OAuth Provider and Drupal as OAuth Client.
How to perform the SSO login?
- Now, open a new browser/private window and go to your Drupal site login page.
- Click on the Login using Azure link to initiate the SSO from Drupal.
-
If you want to add the SSO link to other pages as well, please follow the steps given in the image below:
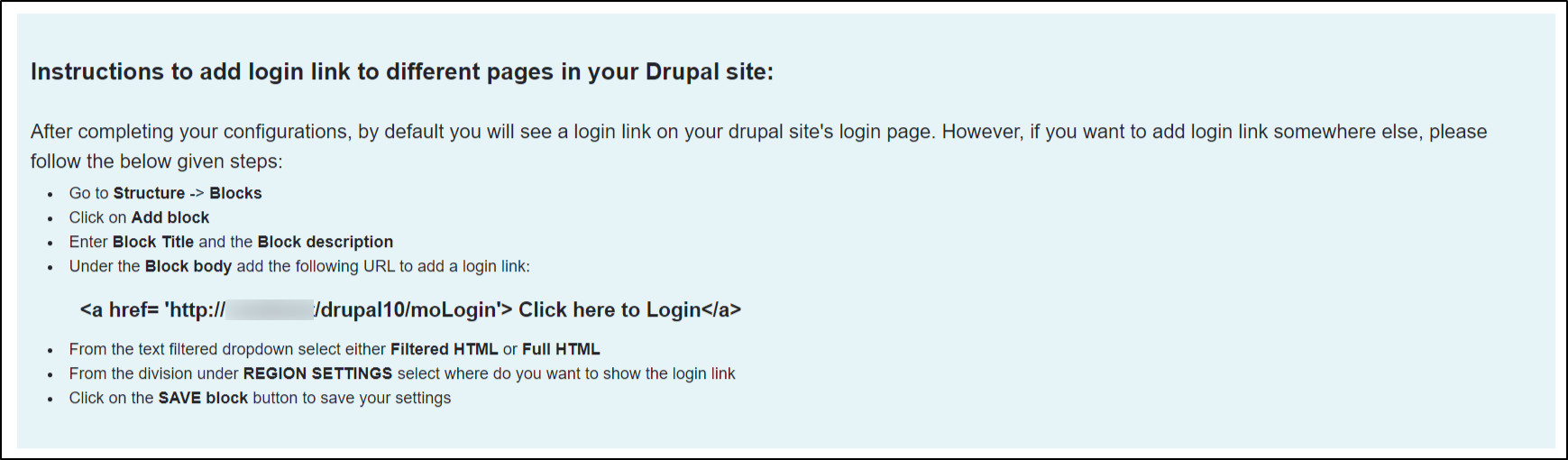
Help improve this page
You can:
- Log in, click Edit, and edit this page
- Log in, click Discuss, update the Page status value, and suggest an improvement
- Log in and create a Documentation issue with your suggestion
 Support for Drupal 7 is ending on 5 January 2025—it’s time to migrate to Drupal 10! Learn about the many benefits of Drupal 10 and find migration tools in our resource center.
Support for Drupal 7 is ending on 5 January 2025—it’s time to migrate to Drupal 10! Learn about the many benefits of Drupal 10 and find migration tools in our resource center.










