 Support for Drupal 7 is ending on 5 January 2025—it’s time to migrate to Drupal 10! Learn about the many benefits of Drupal 10 and find migration tools in our resource center.
Support for Drupal 7 is ending on 5 January 2025—it’s time to migrate to Drupal 10! Learn about the many benefits of Drupal 10 and find migration tools in our resource center.The core idea of Cartaro is the closest possible integration of geodata with other content in a single software stack. This aspect also extends to the common management of users, roles and their permissions, meaning you should be able to apply the same security mechanisms and permissions for spatial and non-spatial content. Within Cartaro the permissions for non-spatial content are handled by Drupal. GeoServer, on the other hand, is responsible to deliver optionally protected geospatial data to the web either through web services (OWS) or through a number of downloadable file formats.
A GeoServer extension is provided in order to use Drupal as user and role provider for GeoServer allowing Cartaro to forward Drupal authorizations to GeoServer. This means you can set up a protected geo web service with GeoServer that is automatically available to a user after login into the Drupal site.
Further the same GeoServer provided service is available outside of your Drupal site too, e.g. in a Desktop GIS connecting to GeoServer directly. The usual authentication mechanisms as defined by the OGC and implemented by GeoServer apply but do respect any permissions set in Drupal (those are merged with the permissions you set in GeoServer).
Even though setting GeoServer up this way is optional we do strongly recommend doing so as it automates user/permission synchronization which is an error prone process if done by hand.
Installing the GeoServer extension
Be sure to met the GeoServer prerequisites referred in the Cartaro installation related with the JVM startup parameters and the session timeout of GeoServer. A Drupal/PostGIS datasource (store) and its workspace should exist before. These should have been created automatically in a normal Cartaro installation.
The GeoServer extension is provided as a JAR file. The geoserver-sec-drupal-7.x-x.x.jar version should match the Cartaro version. For example, for cartaro-7.x-1.0 we will use geoserver-sec-drupal-7.x-1.0.jar version. It needs to be placed in GeoServer folder geoserver/WEB-INF/lib/. In case you use Tomcat to run GeoServer the path will be similar to /var/lib/tomcat7/webapps/geoserver/WEB-INF/lib/.The geoserver-sec-drupal-7.x-x.x.jar file owner and group must be set to Tomcat.
A classpath modification is used to override GeoServer's default implementation. Open WEB-INF/web.xml and append classpath*:/applicationSecurityContextOverride.xml to the contextConfigLocation context parameter. This parameter sets where Spring (GeoServer's authentication and access-control framework) looks for implementations of classes. The later a configuration is read, the more prioritized it is. Restart GeoServer so that it picks up the new classes.
<context-param>
<param-name>contextConfigLocation</param-name>
<param-value>classpath*:/applicationContext.xml classpath*:/applicationSecurityContext.xml classpath*:/applicationSecurityContextOverride.xml</param-value>
</context-param>
Adding a Drupal Role Service
A Role Service is a source of roles or granted authorities for users and groups. At any given time only a single role service may be active. The active role service is used by User-Group Services when loading user information to determine what roles to grant to a user.
As we want Drupal as a role provider for Geoserver, we need to add a new role service of type Drupal. First, log into GeoServer using a user with ADMIN role. In Security → Users, Groups, Roles → Role Services click on Add new.
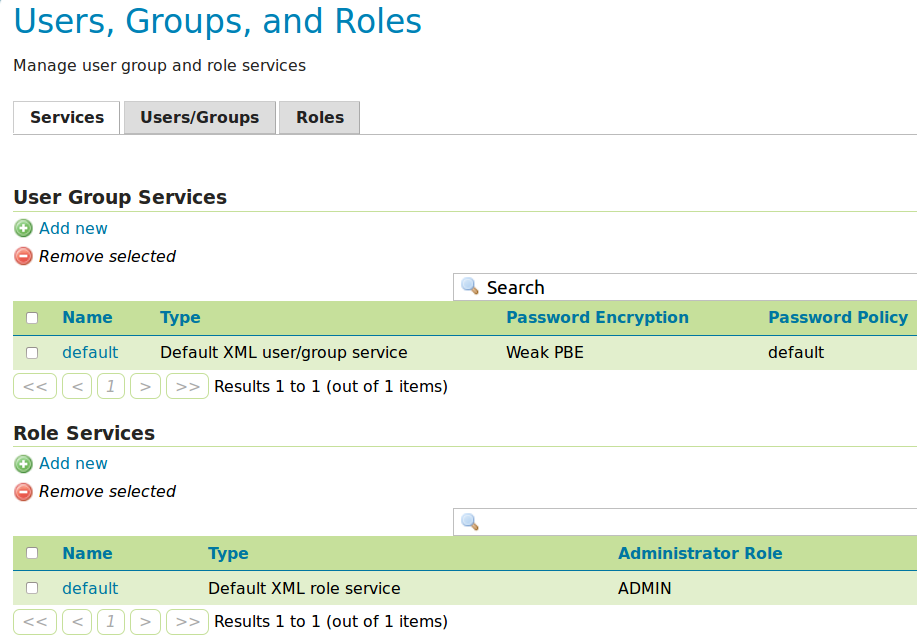
Choose a Role Service of type Drupal and set any name for it. Only one such service is enough for any number of bound Drupal instances.
Finally make sure GeoServer does actually use the new service by selecting it in GeoServer's global security settings.
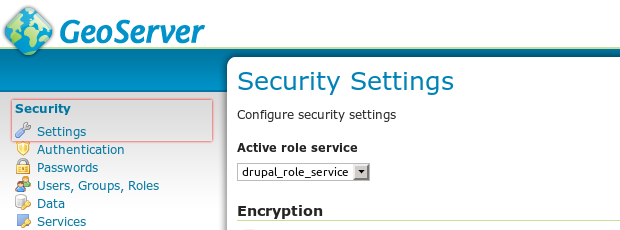
Binding Drupal instances
Each Drupal instance whose users and roles should be available in GeoServer needs to be added, too. To do so add an Authentication Provider of type Drupal by clicking Add new in Security → Authentication → Authentication Providers.
Choose any name for your Drupal instance and enter the connection parameters for its database. The user you set here needs to be able to read users and roles from the Drupal database. GeoServer will use it to verify credentials and to read the roles for each authenticated user. If GeoServer is shared by multiple Cartaro instances it is necessary to check the Usernames are prefixed option to make Drupal instances distinguishable in GeoServer.
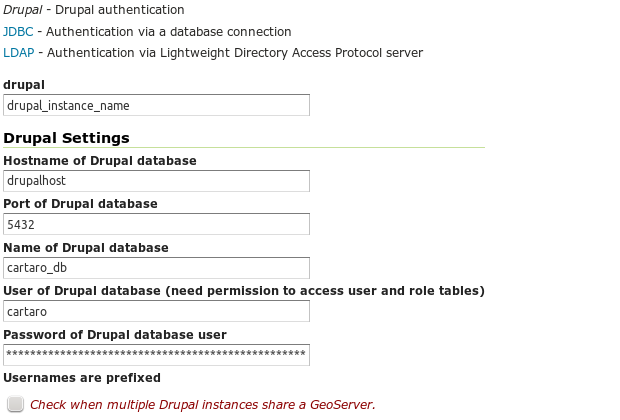
Each Drupal instance needs its own User-Group Service. A User-Group Service is a source of information for users, passwords, and group affiliation. Add a User-Group Service clicking Add new in Security » Users, Groups, Roles » User Group Services.
The name of the new User-Group Service should be the same that the Workspace name that you choose when installing Cartaro. The database credentials should be the same as used for the Authentication Provider. Password Encryption can be set as plain text since Drupal hashes passwords itself and Password policy can be set as default. More info about password management inside GeoServer can be found in GeoServer documentation.
Activate the authentication provider by moving it into the list of active providers (Security → Authentication → Authentication Providers). GeoServer will now acquire a database connection to your Drupal instance and accept Drupal users for login thereafter.

Login into GeoServer
As long as you are using your browser to access Cartaro there is no need to bother about logging into GeoServer. Cartaro will take care that you are logged into GeoServer as well when logging into Cartaro which allows access to all maps where your user has been granted by the permission settings within Drupal.
Simply use the same user name and password as for logging into Cartaro when accessing GeoServer's web services from a third-party application. This applies in case you want to access GeoServer from a desktop GIS for feature editing over WFS for example.
Note that you need to prepend your Drupal user name with Cartaro's workspace if, and only if, your GeoServer is shared by multiple Cartaro instances. For example if the GeoServer workspace used by Cartaro is called forestry and your Drupal user is pat, your desktop GIS would need to use forestry_pat as user name. Your password is unaltered. Prefixing user names and roles in GeoServer provides that the Cartaro instances are distinguishable in GeoServer in such case.
See geoserver-sec-drupal's readme for more detailed instructions.











Comments
classpath modification instruction a bit unclear
The final resulting script and how it should look would be helpful as an illustration as I can think of more than one likely script here.
What would result seems to be classpath*:/applicationSecurityContextOverridecontextConfigLocation.xml is what you get with append.
Thanks for the hint. The
Thanks for the hint. The relevant fragment of the configuration you end up with is:
Please refer to Spring's documentation for in depth information.
Update to match cartaro version1.8 in sight?
Hi guys,
i really like cartaro , cool stuff!
Anyhow, are there efforts to update the geoserver extension to match cartaro 1.8 and geoserver 2.6 ?
Best,
R