Support for Drupal 7 is ending on 5 January 2025—it’s time to migrate to Drupal 10! Learn about the many benefits of Drupal 10 and find migration tools in our resource center.
Support for Drupal 7 is ending on 5 January 2025—it’s time to migrate to Drupal 10! Learn about the many benefits of Drupal 10 and find migration tools in our resource center.This project is not covered by Drupal’s security advisory policy.
When uploading files to the local file store on the server drupal defaults to disallowing symlinked locations outside of the document root.
This is a security feature which is designed to prevent file uploads being crafted to give access to system files.
When files are saved a 'streamwrapper' is called which handles the saving of the file and also does the check for symlinked folders
This module creates a new streamwrapper based on the core DrupalPublicStreamWrapper and overrides the function getLocalPath($uri=null)
When implemented it is enough to choose "symlinked document store" for your file field
The file will then be saved into the symlinked folder without the usual errors
The code in this module is based on the patch found here
https://www.drupal.org/node/1008402#comment-9065341
Currently this code works in Drupal 7 only.
REQUIREMENTS
------------
- Fields (core) module
HOW TO INSTALL
--------------
- Copy folder to sites/all/modules
- Browse to admin/modules in your browser
- Enable Symlink Paths in the Stream Wrappers section
HOW TO USE
----------
- When the module is installed and enabled creating a new file field in your content type will give you the option to store files in either public: private: or symlinked document store choose "symlinked document store"
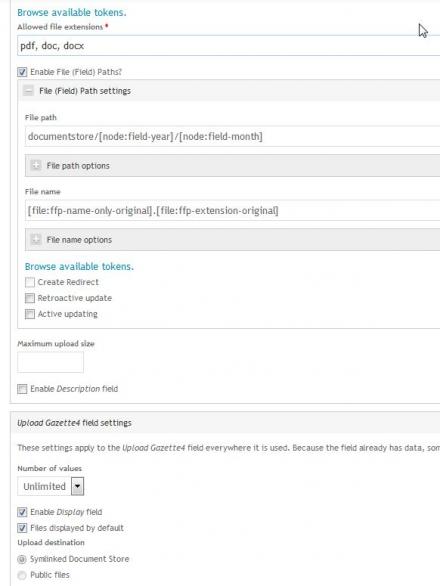
- put the storage path into your file field settings (see example image)
- Create a symlink in your files folder e.g.
sites/default/files/documentstore -> /documentstore - Make sure your symlinked folder is writeable by the webserver
- Now when you upload a file to your server it will be copied to the appropriate folder.
- Make sure your webserver will follow symlinks for example in apache you need the configuration setting "Options FollowSymLinks"
See example settings image. Please note the example uses the filefield_paths module for token replacement
Project information
- Module categories: Media
- Created by DeveloperChris on , updated
This project is not covered by the security advisory policy.
Use at your own risk! It may have publicly disclosed vulnerabilities.